What is Annabelle ransomware? And how does it carry out its malicious attack?
Annabelle ransomware is another file-encrypting threat that is based on the Stupid ransomware virus. This new ransomware Trojan is discovered by a security researcher named Bart. As soon as this dangerous ransomware infects your computer, it will configure itself to automatically start when you log in to your Windows PC. It then terminates a couple of programs on your computer such as Process Hacker, Process Explorer, Msconfig, Task Manager, Chrome, etc. In addition, it also terminates a number of security programs, turn off the firewall and disable Windows Defender.
On the next phase of its attack, Annabelle ransomware configures the Image File Execution registry entries so that you won’t be able to launch various programs on your system like the ones mentioned above and other programs like Notepad ++, Notepad, Internet Explorer, Opera, bcedit and so on. Following this malicious activity, this crypto-malware will try to spread itself using autorun.inf files – this kind of tactic is actually of no use when it comes to newer versions of Windows that do not have the autoplay feature. After that, Annabelle ransomware will start to encrypt its targeted files with a static key and then append the .ANNABELLE extension once it’s done with the encryption. It then reboots the affected computer so that when you log back into your computer, it will display a lock screen which has credits button. When you click on that particular button the screen will show a developer named “iCoreX0812” created the malicious program as well as a way to contact the crooks behind this formidable threat.
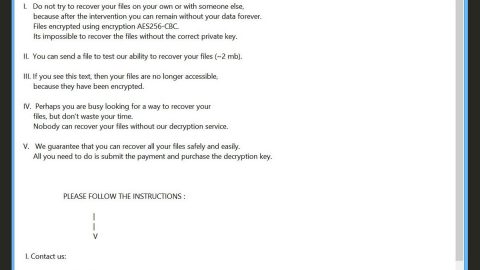
In the final phase of its attack, Annabelle ransomware will run a program that replaces the master boot record of the infected PC to display a “props” screen as soon as the PC reboots. Moreover, Annabelle ransomware also displays the following ransom note on the infected PC:
“What Happened to my files?
All your files are encrypted and secured with a strong key. There is no way to get them back without your personal key.
How can I get my personal key?
Well, you need to pay for it. You need to visit one of the special sites below & then you need to enter your personal ID (you find it on the top) & buy it. Actually, it costs exactly 0.1 Bitcoins.
How can I get access to the site?
You easily need to download the Torbrowser, you can get it from this site:
https://www.torproject.org
What is going to happen if I’m not going to pay?
If you are not going to pay, then the countdown will easily run out and then your system will be rboken. If you are going to restart, then the countdown will run out a much faster. So, it’s not a good idea to do it.
I got the key, what should I do now?
Now you need to enter your personal key in the textbox below. Then you will get access to the decryption program.
– The darknet sites are not existing, its just an example text. The other things are right, except the darknet thing. Its possible to get the key, but if I going to do a new trojan, or the new version of this then I will add real ways to get the key 🙂 If you wanna that I going to do a 2.0 or a new trojan, then write it below in the comments. Thanks
If you wanna chat with me, contact me easily in discord: iCoreX#1337”
How is Annabelle ransomware disseminated over the web?
Just like other ransomware threats, Annabelle ransomware is disseminated over the web via spam emails, malware-laden advertisements, fake software and fake software updates as well as exploit kits.
Carefully follow the given removal guide below to successfully eliminate Annabelle ransomware from your PC.
Step 1: Reboot your computer into Safe Mode with Command Prompt by pressing F8 a couple of times until the Advanced Options menu appears.

Navigate to Safe Mode with Command Prompt using the arrow keys on your keyboard. After selecting Safe Mode with Command Prompt hit Enter.
Step 2: After loading the Command Prompt type cd restore and hit Enter.

Step 3: After cd restore, type in rstrui.exe and hit Enter.

Step 4: A new window will appear, and then click Next.

Step 5: Select any of the Restore Points on the list and click Next. This will restore your computer to its previous state before being infected with the Annabelle Ransomware.
Step 6: A dialog box will appear, and then click Next.

Step 3: After System Restore is completed, log into your computer and tap Ctrl + Shift + Esc keys to launch the Task Manager.
Step 4: Go to Processes and look for Annabelle ransomware’s malicious process such as Copter.flv.exe and MBRiCoreX.exe, right click on it and select End Process or End Task.

Step 4: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 5: Look for dubious programs that might be related to Annabelle ransomware and then Uninstall it/them.

Step 6: Tap Win + E to launch File Explorer.
Step 7: After opening File Explorer, navigate to the following locations below and look for Annabelle ransomware’s malicious components such as the macro-enabled document, the Copter.flv.exe and MBRiCoreX.exe malicious executable files and then delete all of them.
- %UserProfile%\AppData
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
- %TEMP%.
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 8: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 9: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 10: Navigate to the listed paths below and look for the registry keys and sub-keys created by Annabelle ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 11: Delete the registry keys and sub-keys created by Annabelle ransomware.
Step 12: Close the Registry Editor and empty the Recycle Bin.
Follow the continued advanced steps below to ensure the removal of Annabelle Ransomware:
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS scren will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. The installation will start automatically once a download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click the REMOVE ALL

Register the program to protect your computer from future threats.