What is RansomAES ransomware? And how does it carry out its attack?
RansomAES ransomware is a file-encrypting virus that’s been targeting Korean users as of late. It is created to encrypt important files in a system and urge victims to pay the ransom demanded. The files encrypted by this crypto-malware can be easily recognized as each affected files contain the extension “.RansomAES”. According to researchers, RansomAES ransomware is a variant of both the RansomAES and Spartacus ransomware. As per the researchers who analyzed the code of this crypto-malware, they’ve found that most of its code is the same as the aforementioned ransomware threats.
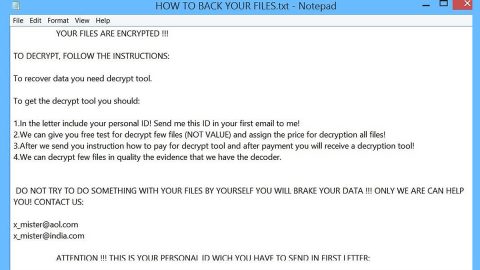
RansomAES ransomware, upon infiltration, could make changes in the Windows system files and processes and even make additional entries and modify existing ones in the Windows Registry. And when it starts its encryption, it mostly targets user-generated files using both the AES and RSA encryption algorithms. After the encryption, it drops a file named “READ ME.txt” which contains its ransom note written in Korean:
“당신의 파일이 암호화되었습니다! 당신에 확장자: .AES 이메일로 요청드리면 복구해드립니다. [email protected] 또는
[email protected] 개인 ID KEY:”
Aside from its ransom note, RansomAES ransomware also displays a GUI window which also contains a ransom note that states:
“RansomAES
당신의 모든 파일이 암호화되었습니다!
당신의 파일이 암호화되었습니다! 당신에 확장자: .AES 이메일로 요청드리면 복구해드립니다. [email protected] 또는
[email protected]
Bitcoins 에서 암호 해독에 대한 비용웁 지害해야합니다. 가격은 당신이 우리에게 어떻게 쓰는지에 달려 있습니다. 지뜰 후 우리는 당신에개
모든 파일을 해독할수 었는 해독 도구를 드립니다.
지올 위에 있는 개인 ID는 저희 이메일로 ID를 클립으로 복사해서 ID률 주세요.”
Here’s an English translation of the ransom note:
“RansomAES
All your files have been encrypted!
Your file has been encrypted! You will receive the extension: .AES email and we will repair it. [email protected] or
[email protected]
The cost for decryption in Bitcoins should be harmful. The price depends on how you use it for us. After the courtyard, we have dogs on you
We provide decryption tools that can decrypt all files.
Please copy the ID of the personal ID above the paper to our e-mail.”
As you can see, it is evident that these two email address, [email protected], and [email protected], are being used as a means for victims to contact the crooks behind RansomAES ransomware. However, if you are one of the victims of this ransomware threat, contacting these crooks and paying the ransom is not advised.
How does RansomAES ransomware proliferate?
RansomAES ransomware proliferates using malicious spam emails infected with a corrupted attachment that’s used to install RansomAES ransomware in the targeted machine. That’s why if you see any suspicious-looking email, do not hesitate to delete it from your inbox as it might be the malicious payload of ransomware threat like RansomAES ransomware.
Use the removal guide below as a reference to wiping out RansomAES ransomware from your computer.
Step 1: The first thing you have to do is to close the GUI window of RansomAES ransomware. If you’re not able to close it manually, you can do so by tapping Ctrl + Shift + Esc keys to launch the Task Manager.
Step 2: Go to Processes and look for the malicious process of RansomAES ransomware named “RansomAES.exe” then right click on it and select End Process or End Task.

Step 3: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 4: Look for dubious programs that might be related to RansomAES ransomware and then Uninstall it/them.

Step 5: Tap Win + E to launch File Explorer.
Step 6: From there, navigate to the following directories listed below and look for the malicious components of RansomAES ransomware like RansomAES.exe and READ ME.txt and remove them all.
- %TEMP%
- %APPDATA%
- %DESKTOP%
- %USERPROFILE%\Downloads
- C:\ProgramData\local\
Step 7: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name], this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 8: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 9: Navigate to the listed paths below and look for the registry keys and sub-keys created by RansomAES ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 10: Delete the registry keys and sub-keys created by RansomAES ransomware.
Step 11: Close the Registry Editor.
Step 12: Empty your Recycle Bin.
Try to recover your encrypted files using the Volume Shadow copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if RansomAES ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

Complete the removal process of RansomAES ransomware by using a trusted and reliable program like [product-name]. Refer to the following guidelines on how to use it.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen wll be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.