What is Pennywise ransomware? And how does it execute its attack?
Pennywise ransomware is a file-encrypting Trojan infection that was discovered in the last week of October this year. Pennywise ransomware appears to be another variant of the infamous Jigsaw ransomware which first emerged way back in April 2016 – since then, the Jigsaw group of crypto-malware has expanded and Pennywise is just one of the latest variant of this group of ransomware threats, among them are HACKED ransomware, StrutterGear ransomware and many more.
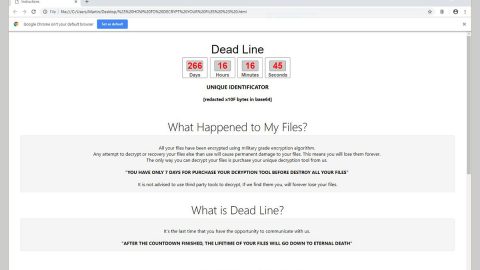
Pennywise ransomware was found in an online security platform where malware security experts exchange samples, notes and keep an eye on the latest trends in the threat development. According to these experts, it seems that Pennywise ransomware is still under development and that evidence of the ransomware suggests that it could still be on its debug and testing phase. As you can see on the screenshot above, creators of this ransomware makes use of the image of a scary clown known as Pennywise in branding this threat. Based on the code analysis made out of this ransomware, it revealed that this ransomware creates a folder on the primary system disk which is at C:\FileSystemStimulation\. The malware uses the location so that it can load on the system. And based on the lab tests conducted by security researchers, Pennywise ransomware uses the following files to facilitate its tasks:
- exe
- txt
- nottxt
- txt
- txt.beep
After infiltrating the system it targets and encrypts files with the following formats:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
It then appends the .beep extension to each one of the files. And then generates a program window that delivers the following ransom note to the its victims:
“Your personal files are being deleted. Your photos, videos, documents, etc…
But, don’t worry! It will only happen if you don’t comply.
However I’ve already encrypted your personal files, so you cannot access them.
Every hour I select some of them to delete permanently, therefore I won’t be able to access them, either.
If you turn off your computer or try to close me, when I start next time you will get 1000 files deleted as a punishment.
Yes you will want me to start next time, since I am the only one that is capable to decrypt your personal data for you.
Meanwhile….. You want a balloon? Hahahahaha_”
How does Pennywise ransomware spread its malicious payload?
It isn’t clear yet how Pennywise ransomware spreads its malicious payload but security experts are sure that it spreads them using the most common method of distribution which is through malicious spam email campaigns. Developers of Pennywise ransomware add an infected or corrupted attachment to the email. Once this attachment is downloaded and opened, Pennywise ransomware will be installed in the computer which is why it is important that you refrain from opening any attachments you receive online especially if the sender is unknown.
Step1. Open the Task Manager simply by tapping Ctrl + Shift + Esc keys on your keyboard.
Step2. Under the Task Manager, go to the Processes tab and look for any suspicious-looking process which takes up most of your CPU’s resources and is most likely related to Pennywise ransomware.

Step3. After that, close the Task Manager.
Step4. Tap Win + R, type in appwiz.cpl and click OK or tap Enter to open Control Panel’s list of installed programs.
Step5. Under the list of installed programs, look for Pennywise ransowmare or anything similar and then uninstall it.

Step6. Next, close Control Panel and tap Win + E keys to launch File Explorer.
Step7. Navigate to the following locations below and look for Pennywise ransomware’s malicious components such as Setup.exe, EncryptedFileList.txt, NotTextTest.nottxt, TxtTest.txt and TxtTest.txt.beep as well as other suspicious files and then delete all of them.
- %TEMP%
- %APPDATA%\Microsoft\Windows\Templates\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step8. Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step9. Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step10. Navigate to the following path:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKCU\SOFTWARE
- HKCU\SOFTWARE\WOW6432Node
Step11. Delete the registry keys and sub-keys created by Pennywise ransomware.
Step12. Close the Registry Editor and empty your Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if Pennywise ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

It is important to make sure that nothing is left behind and that Pennywise ransomware is completely removed use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOSscreen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Optionuse the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Boxwill show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.