What is FORMA ransomware? And how does it implement its attack?
FORMA Ransomware is a file-encrypting virus designed to lock important data in a computer. This cryptovirus is created based on the open-source platform called HiddenTear. It was first discovered on December 11, 2018, and seems to be targeting Polish-speaking users based on its ransom note which is written in Polish.
FORMA ransomware runs as a malicious executable file named “FORMA.exe”. Once this malicious file is executed, FORMA ransomware will begin to implement a series of changes in the system. It starts by connecting it to a remote server controlled by the cybercriminals behind FORMA ransomware. After that, it downloads tons of its components from this remote server, namely:
- ODSZYFRFUJ_PLIKI_TERAZ.txt
- 1.bat
- 2.bat
- 3.bat
- 4.bat
- admin.exe
- adobeacrobatreader.exe
- forma.exe
- invisible.vbs
- ystemkey.txt
- winsys.txt
- winsys2.txt
- winsys3.txt
- table.exe
- cabacca.tmp
- taraccb.tmp
- syswin32.lnk
- [random].exe
After it places its malicious components in system folders, FORMA ransomware will modify the Windows Registry so that it can resume its attack every time a victim turns on the infected computer. It also launches and represses system processes making it a persistent threat. Aside from that, it also employs a data gathering module and stealth protection module. The first module is used to obtain information from the computer that will be used for the next module. The second module is used to prevent any security and antivirus programs from interrupting the attack. Once the system modifications are completely implemented, FORMA will start encrypting its targeted files such as:
.avi, .bmp, .doc, .docx, .html, .jpeg
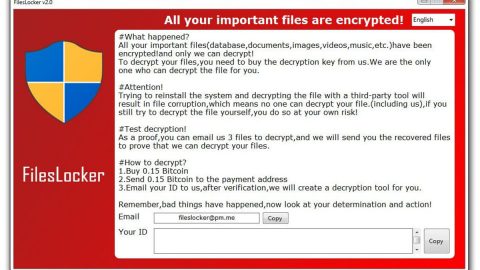
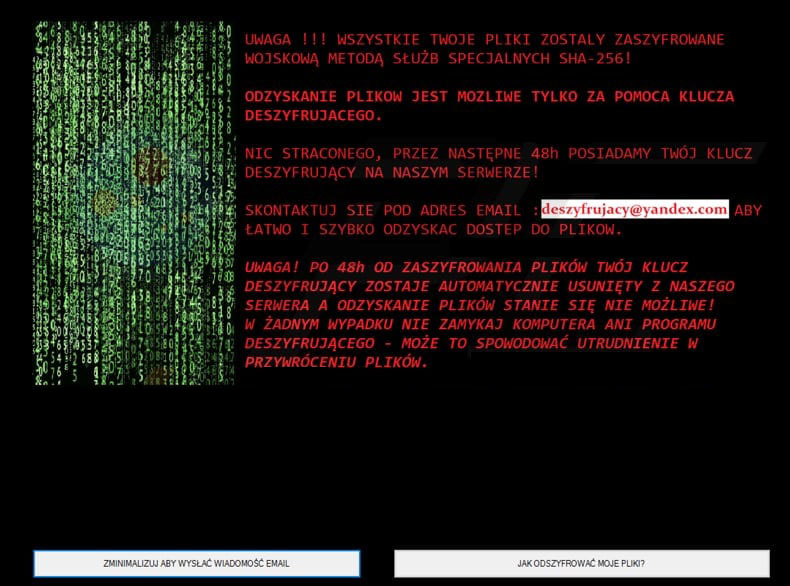
It encrypts its targeted files using a custom AES 256 encryption algorithm. After the encryption, FORMA ransomware will open its ransom which is written in the Polish language. Here’s an English translation of its ransom note:
“ATTENTION !!! ALL YOUR FILES WERE CALLED WITH A CHARACTER KEY! RECOVERY OF FILES IS POSSIBLE ONLY WITH THE AID OF A DESZYRUIZING KEY. NOTHING LOST, BY THE NEXT 48h, WE HAVE YOUR KEY THAT IS TRANSFERS ON OUR SERVER! CONTACT EMAIL ADDRESS: [email protected] TO RECOVER ACCESS TO FILES – ATTENTION! AFTER 48 HOURS FROM FILE ERADING, YOUR SATISFACTION KEY IS AUTOMATICALLY DELETED FROM OUR SERVER AND THE RECOVERY OF FILES IS NOT POSSIBLE. IN NO EVENT, DO NOT CLOSE A COMPUTER OR A DESIRACKING PROGRAM – IT MAY CAUSE THE IMPROVEMENT IN THE RETRIEVATION OF FILES. WE GUARANTEE THE RECOVERY OF ALL FILES!”
If you are one of the unlucky users whose files are compromised by FORMA ransomware, writing to [email protected] is not recommended for these crooks might only give you false promises and you’ll end up losing money for nothing. The best thing you can do to deal with such a cyber threat is to wipe it out from your computer right away and then use an alternative way (which will be provided later on) to recover your encrypted files.
How does FORMA ransomware proliferate?
FORMA Ransomware proliferates using malicious spam email campaigns. Cybercriminals attach an infected files as attachments and send them to potential victims. This infected file contains scripts used to install FORMA ransomware in the system.
Make use of the removal instructions provided below to wipe out FORMA ransomware from your computer.
Step_1: Tap Ctrl + Shift + Esc keys to launch the Task Manager.
Step_2: Go to Processes and look for the malicious processes of FORMA ransomware like FORMA.exe. Note that these processes usually take up most of the CPU power so once see an unusual process, right-click on it and select End Process or End Task.
Step_3: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step_4: Look for dubious programs that might be related to FORMA ransomware and then Uninstall it/them.
Step_5: Close Control Panel and tap Win + E to launch File Explorer.
Step_6: After opening File Explorer, navigate to the following directories below:
- \ Desktop \ ->
- \ User_folders \ ->
- \% TEMP% \ ->
- % TEMP% \ 1.bat
- % TEMP% \ 2.bat
- % TEMP% \ 3.bat
- % TEMP% \ 4.bat
- % TEMP% \ admin.exe
- % TEMP% \ adobeacrobatreader.exe
- % TEMP% \ forma.exe
- % TEMP% \ invisible.vbs
- % HOMEPATH% \ systemkey.txt
- % HOMEPATH% \ winsys.txt
- % HOMEPATH% \ winsys2.txt
- % HOMEPATH% \ winsys3.txt
Step_7: From the directories listed above, look for the following files of FORMA ransomware and delete all of them.
- ODSZYFRFUJ_PLIKI_TERAZ.txt
- 1.bat
- 2.bat
- 3.bat
- 4.bat
- admin.exe
- adobeacrobatreader.exe
- forma.exe
- invisible.vbs
- ystemkey.txt
- winsys.txt
- winsys2.txt
- winsys3.txt
- table.exe
- cabacca.tmp
- taraccb.tmp
- syswin32.lnk
- [random].exe
Step_8: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech-savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you trouble and time, you can just use Restoro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step_9: Tap Win + R to open Run and then type in Regedit in the field and tap enter to pull up Windows Registry.
Step_10: Navigate to the listed paths below and look for the registry keys and sub-keys created by FORMA ransomware.
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step_11: Delete the registry keys and sub-keys created by FORMA ransomware.
Step_12: Close the Registry Editor and empty the contents of Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows Previous Versions feature will only be effective if FORMA ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.
Congratulations, you have just removed FORMA Ransomware in Windows 10 all by yourself. If you would like to read more helpful articles and tips about various software and hardware visit fixmypcfree.com daily.
Now that’s how you remove FORMA Ransomware in Windows 10 on a computer. On the other hand, if your computer is going through some system-related issues that have to get fixed, there is a one-click solution known as Restoro you could check out to resolve them.
This program is a useful tool that could repair corrupted registries and optimize your PC’s overall performance. Aside from that, it also cleans out your computer for any junk or corrupted files that help you eliminate any unwanted files from your system. This is basically a solution that’s within your grasp with just a click. It’s easy to use as it is user-friendly. For a complete set of instructions in downloading and using it, refer to the steps below
Perform a full system scan using Restoro. To do so, follow the instructions below.