What is GPGQwerty ransomware? And how does it carry out its attack?
GPGQwerty ransomware is a new crypto-malware first spotted in the first week of March 2018. This new ransomware threat utilizes the legitimate GnuPG or GPG – an encryption program – to encrypt victims’ files. In other words, GnuPG is a legitimate program being used illegally by the cyber crooks that developed GPGQwerty ransomware. Although these crooks aren’t the first ones who used this legitimate program in such a way as it has been done in the past by developers of VaultCrypt KeyBTC ransomware, it is still not something that happens every so often.
GPGQwerty ransomware consist of a package of individual files that are run together and used in carrying out the attack on the targeted computer. The package is made up of the GnuPG gpg.exe, gnuwin32 shred.exe, a batch file used to load the keys and launch a JS file, and run.js – JS file used to execute the find.exe program. The first file this crypto malware launches is the key.bat file that acts as the main launcher for GPGQwerty ransomware as it sequentially executes several commands. After the batch file is run, the keys will be imported then the batch files will launch run.js – used in executing the find.exe program – the main component of GPGQwerty ransomware.
During the execution of find.exe program, it will specify a particular drive letter that it is trying to encrypt. Following the execution of find.exe, it will launch a series of commands that are listed below.
- taskkill /F /IM sql /T
- taskkill /F /IM chrome.exe /T
- taskkill /F /IM ie.exe /T
- taskkill /F /IM firefox.exe /T
- taskkill /F /IM opera.exe /T
- taskkill /F /IM safari.exe /T
- taskkill /F /IM taskmgr.exe /T
- taskkill /F /IM 1c /T
- exe delete shadows /all /quiet
- wmic shadowcopy delete
- exe bcdedit /set {default} bootstatuspolicy ignoreallfailures
- exe bcdedit /set {default} recoveryenabled no
- exe wbadmin delete catalog –quiet
- del /Q /F /S %s$recycle.bin
Once the aforementioned commands are executed, GPGQwerty ransomware will begin to encrypt files. It is still not known what type of files this ransomware targets. However, it might encrypt popular files like images, documents, audio, videos, and so on.
This crypto-malware uses the command “gpg.exe –recepient qwerty –o “%s%s.%d.qwerty” –encrypt “%s%s”” in encrypting the targeted files. This command also uses the imported public key in encrypting files and save them as new files with the .qwerty extension appended on their new file names. During the encryption, this ransomware encrypts files that do not contain these strings:
- Recycle
- temp
- Temp
- TEMP
- windows
- Windows
- WINDOWS
- Program Files
- PROGRAM FILES
- ProgramData
- gnupg
- .qwerty
- txt
- .exe
- .dll
Following the encryption, GPGQwerty ransomware will run the shred.exe file so it can overwrite the encrypted files. Note that this ransomware only overwrites files once so it is still possible to recover the affected files with the help of a file recovery software. After that, GPGQwerty ransomware will create a ransom note named “README_DECRYPT.txt” and drop it in each folder where there is an encrypted file. It contains a message that states:
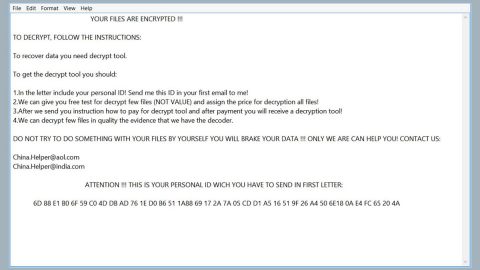
“Your computer is encrypted. All data will be lost if you do not pay 0.1 BTC to the specified BTC wallet 3M3QNTzEpEzFqzUtXZRT5FjG1YWfVDyh9K after payment you will receive the decryption code from this mail
[email protected], send your ID 3782. Before paying you can send to us up to 1 files for free decryption.
Please note: that files must NOT contain valuable information and their total size must be less than 1Mb”
How does GPGQwerty ransomware disseminate its malicious payload?
It isn’t clear yet how this ransomware disseminate its malicious payload but it is possible that it manually installs its malicious payload on a targeted computer by hacking into the Remote Desktop Services.
GPGQwerty ransomware removal guide:
Step 1: Reboot your computer into Safe Mode with Command Prompt by pressing F8 a couple of times until the Advanced Options menu appears.

Navigate to Safe Mode with Command Prompt using the arrow keys on your keyboard. After selecting Safe Mode with Command Prompt, hit Enter.
Step 2: After loading the Command Prompt type cd restore and hit Enter.

Step 3: After cd restore, type in rstrui.exe and hit Enter.

Step 4: A new window will appear, and then click Next.

Step 5: Select any of the Restore Points on the list and click Next. This will restore your computer to its previous state before being infected with the GPGQwerty Ransomware.
Step 6: A dialog box will appear, and then click Next.

Step 7: After System Restore is completed, restart your PC to Safe Mode with Networking.

Step 8: Enable the disabled Windows features.
- Press Win + R keys to launch Run.
- Type in msc in the box and press Enter to open Group Policy.
- Under Group Policy, navigate to:
- User Configuration\Administrative Templates\System
- After that, open Prevent access to the command prompt.
- Select Disable to enable cmd
- Click the OK button
- After that, go to:
- Configuration\Administrative Templates\System
- Double click on the Prevent Access to registry editing tools.
- Choose Disabled and click OK.
- Navigate to :
- User Configuration\Administrative Templates\System>Ctrl+Alt+Del Options
- Double click on Remove Task Manager.
- And then set its value to Disabled.
Step 9: Go to Processes and look for GPGQwerty ransomware’s malicious process such as GnuPG gpg.exe, gnuwin32 shred.exe, run.js and find.exe – right click on each process and select End Task.

Step 10: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter. Look for find.exe related to GPGQwerty ransomware and then Uninstall it.

Step 11: Tap Win + E to launch File Explorer then navigate to the following locations below and look for GPGQwerty ransomware’s malicious components such as GnuPG gpg.exe, gnuwin32 shred.exe, run.js and find.exe and README_DECRYPT.txt then delete them all.
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
- %TEMP%
Step 12: Close File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 13: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 14: Navigate to the listed paths below and look for the registry keys and sub-keys created by GPGQwerty ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 11: Delete the registry keys and sub-keys created by GPGQwerty ransomware.
Step 15: Close the Registry Editor and empty Recycle Bin.
To complete the removal of GPGQwerty ransomware, perform a full system scan using SpyRemover Pro.
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.