What is Yoshikada ransomware? And how does it carry out its attack?
Yoshikada ransomware is another file-encrypting threat that’s been targetting many users since January 2018. This ransomware Trojan carries out a typical ransomware attack – from the moment it enters a targeted system, it would immediately scan it to look for the following file types to encrypt:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .exe, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
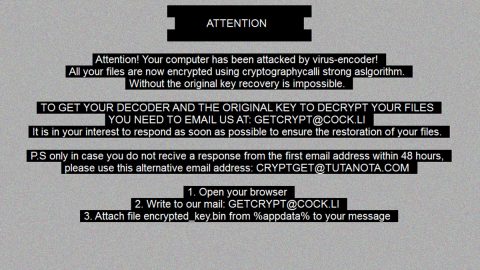
After it finds the targeted files, it will begin the encryption procedure using a combination of AES 256 and RSA 1024 ciphers that would make the files inaccessible to users as the encryption modifies the files with a symmetric key. This entails a single key that could decrypt and encrypt the affected files. However, this key itself is usually encrypted with asymmetric encryption and only the developers of Yoshikada ransomware have access to it. Yoshikada ransomware appends the crypted_yoshikada@cock_lu to the affected files to mark them. It then delivers a ransom note in a text file named “READ_ME.txt” which is placed on the desktop of the infected computer. This ransom note contains the following message:
“Your documents, photos, databases and other important files have been encrypted cryptographically strong, without the original key recovery is impossible! To decrypt your files you need to buy the special software – “YOSHIKADA DECRYPTOR”
Using other tools could corrupt your files, in case of using third party software we don’t give guarantees that full recovery is possible to use it at your own risk. If you want to restore files, write us to the e-mail: [email protected]
In the subject line write “encryption” and attach your personal ID in the body of your message also attach to email 3 crypted files. (files have to be less than 10 MB) It is in your interest to respond as soon as possible to ensure the recovery of your files because we will not store your decryption keys on our server for a long time.”
The developers of Yoshikada ransomware try to be amicable to its victims by offering to decrypt three affected files for free. However, this does not mean that they can be trusted. Even the developers themselves don’t guarantee the full recovery of the files even if the ransom is paid so there really is no point in paying the ransom as it would totally be a waste of money. Instead, you could try other recovery options such as using the shadow volume copies of the files to restore them to their previous state.
How does Yoshikada ransomware distribute its malicious payload?
Yoshikada ransomware distributes its malicious payload through spam emails. The spam emails are usually attached with a malicious executable file used in installing the ransomware to the targeted system. Many users are tricked into downloading this attachment as the emails are disguised as something important like an invoice or receipt or photos. That’s why you need to be cautious when dealing with spam emails and delete any suspicious ones as soon as you spot them.
These are the steps you need to follow to remove Yoshikada ransomware from your PC in case your PC got infected in the future.
Step 1: Tap the Ctrl + Shift + Esc keys to open the Task Manager.

Step 2: After opening the Task Manager, look for Yoshikada’s malicious processes, right click on it and select End Process or End Task.

Step 3: Close the Task Manager.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 4: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 5: Navigate to the following paths:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\Background
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Personalization
- HKEY_CURRENT_USER\Control Panel\Desktop\ScreenSaveTimeOut
- HKEY_CURRENT_USER\Control Panel\Desktop
Step 6: Under the paths listed above, look for registry values created by Yoshikada ransomware like BrowserUpdateCheck which is linked to its corrupted executable file and delete it.
Step 7: Close the Registry Editor and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 8: Look for Yoshikada ransomware or any suspicious program and then Uninstall it/them.

Step 9: Tap Win + E to launch File Explorer.
Step 10: After opening File Explorer, navigate to the following locations below and look for Yoshikada ransomware’s malicious components such as how_to_back_files.html and an executable file named [random].exe then delete them all.
- %TEMP%
- %APPDATA%
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 11: Close the File Explorer.
Step 12: Empty your Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if Yoshikada ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

Make sure that you have completely removed Yoshikada ransomware from your computer, to do so, follow the advanced removal guide below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will bedisplayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. The installation will start automatically once a download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.