What is Paradise ransomware? And how does it execute its attack?
Paradise ransomware appears to be a Ransomware as a Service or a RaaS. Ransomware as a Service is where a ransomware developer creates a ransomware and manages its development as well as operates the Command and Control server in exchange for some small ransom payments it obtains from its victims. Although Paradise ransomware’s activity is still low, the fact that it is distributed as RaaS is a clear sign that other less experienced crooks might pick up its code and further boost its distribution.
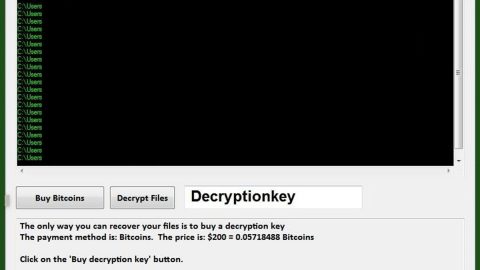
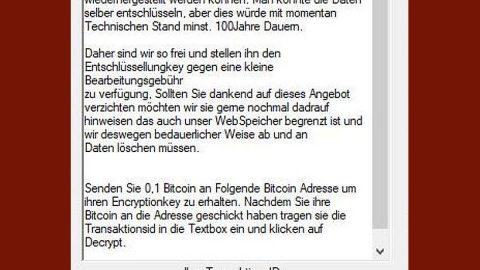
As of now it isn’t determined how Paradise ransomware infects computer but based on the entries in the event log of an infected computer, researchers concluded that it may be through Remote Desktop services. Once executed, the ransomware relaunches itself to obtain administrator privileges and then generate RSA 1024 key which is used to encrypt various files in the compromised computer. During the encryption, it appends the .paradise extension to each file along with the email address. Since Paradise uses RSA encryption, the encryption process is very slow. This is the ideal time for victims to hopefully detect the ongoing encryption and put a stop to it. After that, it drops its ransom note contained in a text file named #Decrypt My Files.txt with a brief description about Paradise ransomware. Here’s the full context of the ransom note:
“[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: [email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller by payment method and price
https://localbitcoins.com/buy_bitcoins
[ATTENTION]
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 36 hours – your key has been deleted and you cant decrypt your files”
Its ransom note does not specify any amount for the ransom but only urges its victims to contact the perpetrators and pay as soon as possible giving its victims at least 36 hours. Regardless of how pressured you are, do not ever try to contact these crooks or even pay the ransom. This won’t actually get you nowhere for there is no guarantee that they will give you the encryption key once they get what they want. You can try out alternative ways to recover your files but before that, make sure that you eliminate the ransomware from your computer first.
How Paradise distribute its malicious files?
Usually, ransomware infections like Paradise distribute its malicious files using spam emails which are often disguised in the form of receipts, invoices, etc. Aside from that it also makes use of RDP attacks to infiltrate your computer which is why you must always keep your antivirus program and your computer system updated to prevent attacks like this.
Eliminate Paradise ransomware using the removal instructions below which also contain instructions as to how to recover your encrypted files.
Step 1: Open Windows Task Manager by pressing Ctrl + Shift + Esc at the same time.

Step 2: Go to both the Application and Processes tabs and look for any suspicious applications and processes and then kill them.

Step 3: Open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 4: Look for Paradise ransomware or any suspicious program and then uninstall it/them.

Step 5: Hold down Windows + E keys simultaneously to open File Explorer.
Step 6: Navigate to the following directories:
- %USERPROFILE%\Desktop
- %USERPROFILE%\AppData\Local\Temp
- %USERPROFILE%\downloads
- %TEMP%
Step 7: Look for the following malicious files created by the ransomware:
- #DECRYPT MY FILES#.txt
- auth
- bmp
- txt
- txt
The next step below is not recommended for you if you don’t know how to navigate the Registry Editor. Making registry changes can highly impact your computer. So it is highly advised to use PC Cleaner Pro instead to get rid of the entries that Paradise ransomware created. So if you are not familiar with the Windows Registry skip to Step 12 onwards.

However, if you are well-versed in making registry adjustments, then you can proceed to step 8.
Step 8: Open the Registry Editor, to do so, tap Win + R and type in regedit and then press enter.
Step 9: Navigate to the path below:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
Step 10: Delete all the Values created by Paradise ransomware.
Step 11: Close the Registry Editor.
Step 12: Empty the Recycle Bin.
Step 14: Try to recover your encrypted files.
Note: Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if Paradise Ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

Follow the continued advanced steps below to ensure the removal of the ransomware infection:
Perform a full system scan using SpyRemover Pro.
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in Apollolocker http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between Apollolocker and http. Click OK.
- A dialog box will be displayed by Internet Apollolocker. Click Run to begin downloading SpyRemover Pro. Installation will start automatically once download is done.
- Click OK to launch the program.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.