What is EggLocker ransomware? And how does it execute its attack?
EggLocker ransomware is a file-encrypting threat that was first seen on March 24, 2018. This ransomware Trojan is supposedly designed to encrypt data and lock the screen of an affected computer. However, according to researchers, this threat does not really encrypt files but only renames them to make them look like they were encrypted. This ransomware wanna-be mostly targets users from the Czech Republic and it seems like it is still under development since it isn’t capable of blocking access to Windows yet and it does not delete the shadow volume copies of the files.
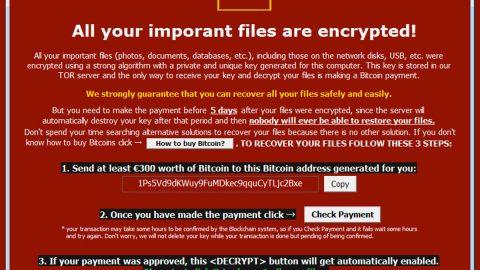
During its attack, EggLocker ransomware runs using a malicious executable file named “EGG.exe” and makes some changes to the system. After that, it pretends to encrypt files by renaming them and adding the “.EGG” suffix to each one of them. It then changes the desktop picture of the infected computer once it’s done renaming the files. The desktop picture contains the following text:
“EGG LOCKED
Your files have been locked due evil
chicken, your only way to get them
back is pay for chicken killers.
Bitcoin address: [redacted]
Any tries to remove chicken will just damage your files.
Be careful with your decisions.”
EggLocker continues its façade by creating a ransom note in a text file named EGG.txt that contains the following message:
“Your Windows might not support this software
Issues
Chicken has just awoken!
Your pc has to pay for all files otherwise
small chicken is going to eat them all!
There is no way to kill a chicken.
Your attack means her respond”
Although EggLocker ransomware isn’t as dangerous as it seems, it does not make it any harmless as its developers could still update it anytime so before that happens, you need to obliterate it from your system right away.
How does EggLocker ransomware proliferate?
At the time of writing, this ransomware threat is not widely distributed yet. Nevertheless, it might use the most common distribution method used by most ransomware developers – spam emails. You need to be cautious about opening or downloading attachments from suspicious-looking emails. Usually, the infected attachment may be an EXE file or a document or a PDF file. Once you open any of these files, the ransomware will be downloaded and installed in the system.
Use the given removal instructions below to obliterate EggLocker ransomware.
Step 1: Tap the Ctrl + Alt + Delete keys to open a menu and then expand the Shutdown options which are right next to the power button.
Step 2: After that, tap and hold the Shift key and then click on Restart.
Step 3: And in the Troubleshoot menu that opens, click on the Advanced options and then go to the Startup settings.
Step 4: Click on Restart and tap F4 to select Safe Mode or tap F5 to select Safe Mode with Networking.
Step 5: After your PC has successfully rebooted, tap Ctrl + Shift + Esc to open the Task Manager.

Step 6: Go to the Processes tab and look for EGG.exe and then end its process.
Step 7: Exit the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 8: Look EggLocker Ransomware and then uninstall it.

Step 9: Close Control Panel and tap Win + E keys to open File Explorer.
Step 10: Navigate to the following locations and look for the malicious components created by EggLocker ransomware such as EGG.txt, the EGG.exe file as well as other files associated to this threat and make sure to delete them all.
- %APPDATA%
- %TEMP%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 11: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name], this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 12: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 13: Navigate to the listed paths below and look for the registry keys and sub-keys created by EggLocker ransomware.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\Background
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Personalization
- HKEY_CURRENT_USER\Control Panel\Desktop\ScreenSaveTimeOut
- HKEY_CURRENT_USER\Control Panel\Desktop
Step 14: Delete the registry keys and sub-keys created by EggLocker ransomware such as info.exe and recovery.txt.
Step 15: After that, close the Registry Editor and empty the Recycle bin.
Restore the previous state of your files using the Shadow Volume copies
Since EggLocker ransomware has messed up the file names of your files, it’s now hard to tell which is which so you have to restore them back to their previous state using their shadow volume copies.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

After you’ve covered the steps provided above, you need to continue the removal process using a reliable program like [product-name]. How? Follow the advanced removal steps below.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.