There are thousands of nuclear devices in the world. And most of these devices are protected by powerful security – patrolling guards, 10 foot thick concrete walls, underground bunkers that can survive a direct bomb impact, and other features.
But nuclear research information is stored on computers. And although the computer security for nuclear devices is always top-notch, it was only a matter of time before talented hackers cracked the code, so to speak.
Unfortunately, it looks like hackers have already been stealing nuclear data across the world for the past few years thanks to a frightening piece of malware called Red October. Check out this map for the infection points and types of data stolen:

Scary, right? That information was compiled by PC antivirus leader Kaspersky, and it shows that governments, banks, and other industries and individuals have all been targeted by the Red October malware.
The scariest part of that data is that it only counts the machines that have installed Kaspersky antivirus. That’s a very small percentage of the total number of computers in each country, so the number of Red October infections is guaranteed to be much higher.
How does the Red October malware work?
Red October relies on exploits discovered by Chinese hackers. These exploits are publicly known, so that doesn’t necessarily mean that china is behind this recent wave of attacks. Instead, Rocra’s programming suggests that it was created by a group of Russian-speaking programmers/hackers.
Red October has been spotted as early as May 2007, which means it has been operating undetected for nearly six years. However, the attacks have hit new highs in each of the last few years and this trend looks to continue in 2013.

The virus is transferred through a web-based Java exploit. This exploit can attack through downloaded email attachments or even a simple visit to a malicious website. So yes, Red October is a big deal and it’s something you should be concerned about.
Source: Kaspersky
Where did Red October come from?
Although the origins of Red October are not known (some are suggesting that it was created by terrorist groups or nation-states). In the past, suspected cyber-terrorist-funding countries have included China, Iran, North Korea, Israel, and the United States. All of those countries have been linked toma
Why is Red October/Rocra so dangerous?
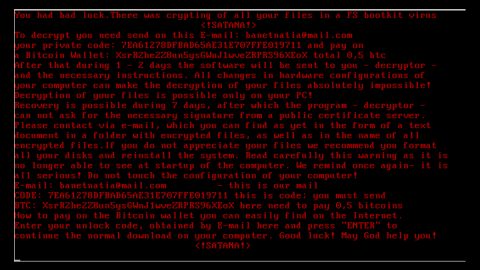
The Red October malware – also known as Rocra – steals data from PC workstations and any devices that are connected to the PC, like a tablet or smartphone. It can also steal data from networks and from removable disks.
But that’s only a small glimpse at what makes Rocra so dangerous. Here are a few other dangerous tasks it can accomplish:
-Steal email messages and attachments
-Record all keystrokes made by the user
-Take screenshots of the infected machine
-Pull history information and cache data from major internet browsers like Chrome, Internet Explorer, Firefox, and Opera
-Steal files from local network FTP servers
-Replicate itself across a local network
That last feature is important. Red October can easily replicate itself across a local network, which means that it can spread very quickly. If your computer has been infected with the Red October virus, then you can expect that other computers on your network have also been infected.

How to avoid the Red October malware
Red October is targeting governments, businesses, and individual PC users around the world. Hopefully, the virus hasn’t hit you yet. To reduce your chances of a Red October infection, be sure to follow these tips:
-Do not download attachments from any known senders (the virus likes to spread this way)
-Don’t visit websites that you don’t know or trust
-Disable Java in your browsers (find out how to do that by reading this article)
-If you work in a government or energy industry-related field, be extra cautious about your computer activities and follow all of the above tips when handling any work-related computers
There’s no 100% effective way to avoid malware. But by following the tips listed above, you can significantly reduce your risk of encountering the deadly Red October malware.