What is Cryakl ransomware? And how does it implement its attack?
Cryakl ransomware emerged anew, but this time, it appends the .fairytail extension on each one of the files it encrypts. This malicious crypto-virus is capable of infiltrating users’ PC using a malicious executable file. After its infiltration, it will quickly scan the infected computer for files to target. Based on the analysis done by security experts, Cryakl ransomware encrypts files which have these extensions:
“.DIF .DIP .DJV .DOC .DOCB .DOCM .DOCX .DOT .DOTM. DOTX .DTD .DWG .DXF .EML .EPS .FDB .FLA .FLV .FRM .GADGET .GBK .GBR .GED .GIF .GPG .GPX .GZ .H .HTM .HTML .HWP .IBD .IBOKS .IFF .INDD .JAR .JAVA .JKS .JOG .JS .JSP .KEY .KML .KMZ .LAY .LAY6 .LDF .LUA .M3U .M4A .M4V .MAX .MDB .MDF .MFD .MID .MKV .MML .PNG .PSD .PSPIMAGE .TGA .THM .TIF .TIFF .YUV .AI .EPS .PS .SVG .INDD .PCT .PDF .XLR .XLS .XLSX .ACCDB .DB .DBF .MDB .PDB .SQL .APK .APP .BAT .CGI .COM .EXE .GADGET .JAR .PIF .WSF .DEM .GAM .NES .ROM .SAV CAD Files .DWG .DXF GIS Files .GPX .KML .KMZ .ASP .ASPX .CER .CFM .CSR .CSS .JS .JSP .PHP .RSS .XHTML .LOG .MSG .ODT .PAGES .RTF .TEX .TXT .WPD .WPS .CSV .DAT .GED .KEY .KEYCHAIN .PPS .PPT .PPTX .INI .PRF Encoded Files .HQX .MIM .UUE .7Z .CBR .DEB .GZ .PKG .RAR .RPM .SITX .TAR.GZ .ZIP .ZIPX .BIN .CUE .DMG .ISO .MDF .TOAST .VCD SDF .TAR .TAX2014 .TAX2015 .VCF .XML Audio Files .AIF .IFF .M3U .MP3 .MPA .WAV .WMA Video Files .3G2 .3GP .ASF .AVI .FLV .MOV .MP4 .MPG .RM .SRT .SWF .VOB .WMV 3D .3DM .3DS .MAX .OBJ R.BMP .DDS .GIF .CRX .PLUGIN .FNT .FON .OTF .TTF .CAB .CPL .CUR .DESKTHEMEPACK .DLL .DMP .DRV .ICNS .ICO .LNK .SYS .CFG”
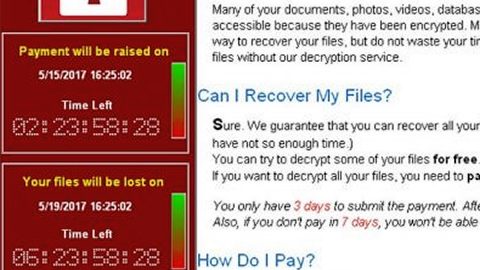
The crypto-malware then begins the encryption procedure by employing both the AES and RSA encryption ciphers making the files almost impossible to decrypt without a decryption key. Once the malware finishes encrypting files, it drops a file named readme.txt and places it on the desktop of the infected PC. The text file contains the ransom note which states:
“All your files have been
encrypted by the Cryakl virus.
All the files were encrypted using
cryptographically strong AES algorithm.
Pay us in Bitcoins to get them back.
You have 72 hours.”
If you are one of the unlucky victims of this new Cryakl ransomware variant, and you’ve been considering making a payment, you have to hold that thought and keep in mind that even if you pay the ransom it surely won’t make any difference as there is no guarantee that the crooks behind Cryakl ransomware will do their end of the bargain once they receive the payment. The best thing you could do is to prioritize the removal of this ransomware infection from your computer and then use Kaspersky’s free Cryakl decryptor on their website.
How does Cryakl ransomware disseminate its malicious payload?
It isn’t clear how the authors of Cryakl ransomware disseminate this ransomware’s malicious payload but according to researchers, it might be done through spam emails. This isn’t surprising as cyber crooks have been using this distribution method for a long time now. The FBI has already been encouraging users to stay alerted and avoid opening spam emails as it might contain harmful ransomware infection.
Refer to the following removal guide to obliterate Cryakl ransomware from your PC.
Step 1: Close the ransom note of Cryakl ransomware and tap the Win + E keys to open File Explorer.
Step 2: Navigate to the following locations and look for a malicious executable file which is randomly named used to install Cryakl ransomware into the computer as well as its ransom note named readme.txt.
- %TEMP%
- %APPDATA%
- %DESKTOP%
- %USERPROFILE%\Downloads
- %HOMEDRIVE%\user | ransom.jpg
- %USERPROFILE%\Desktop | READ_IT.txt
Step 3: Close the File Explorer and tap Ctrl + Shift + Esc keys to open the Task Manager.

Step 4: After opening the Task Manager, look for Cryakl ransomware’s malicious process, right click on it and select End Process or End Task.

Step 5: Close the Task Manager.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 6: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 7: Navigate to the following path:
HKU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Step 8: Look for any suspicious values created by Cryakl ransomware and delete them.
Step 9: Close the Registry Editor and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 10: Look for Cryakl ransomware or any suspicious program and then Uninstall it/them.

Step 11: Empty your Recycle Bin.
Ensure the removal of Cryakl ransomware from your computer as well as the malicious files it created with the help of the advanced removal instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. The installation will start automatically once a download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.













![[LOCKED] Ransomware Crypto thumb](https://fixmypcfree.com/wp-content/uploads/2019/06/LOCKED-Ransomware-Crypto-thumb-480x270.jpg)


