What is Jewsomware ransomware? And how does it implement its attack?
Jewsomware ransomware is another crypto-virus discovered in July 2018. It is designed to lock data in an infected computer. Based on the analysis done by security experts, this crypto-malware is either a joke or a test sample. Meaning to say this threat is not as dangerous as it seems and the files it encrypts are decryptable, at least for now. Even so, its developers might decide to update this threat so it must not be taken lightly.
The instant it is able to infiltrate a targeted computer, it implements a series of changes in the system which allows it to execute its attack without any interference from any programs installed in the computer. It also makes changes in the Windows Registry by modifying some registry entries and sub-keys allowing the crypto-malware to run automatically on every system boot. After that, it starts the encryption process and while doing so, it fills your computer screen with a fake Windows Update screen which cleverly hides the malicious activity in the system. The fake Windows Update screen contains a message saying, “Windows is working on updates”. Once it finishes the encryption, the fake Windows Update screen disappears and is replaced with a red screen containing the following message:
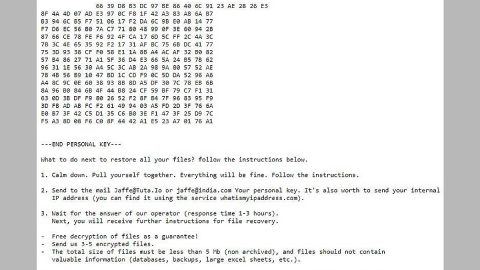
“Your Files Have Been Encrypted by the Sneaky Jew!
To Decrypt them just follow these steps:
– Send 300 € in Bitcoin to this address:
h214ig1e8dsaaIGF2gf9F
– Send your Bitcoin address and your ID to this email:
a9gfa9gh©protonmail.com
– Wait until you receive your Decryption key and
enter it below
– Click Decrypt and wait until it’s finished
– Restart your computer
ID: oDQ1Ev7wU
Decrypt”
If you are one of the victims of Jewsomware ransomware, you need not worry as you can recover your files without paying the ransom. Thus, you must not listen and follow these crooks’ demands and focus on wiping out Jewsomware ransomware from your computer instead.
How does Jewsomware ransomware spread online?
Jewsomware ransomware may spread using malicious spam emails where there is an attached file. This infected attachment may be an executable file or a PDF file or a ZIP file that once opened, will automatically install Jewsomware ransomware in the computer. Therefore, you must double check your emails first before opening any kind of attachment.
With the help of the removal guide prepared below, wipe out Jewsomware ransomware from your computer.
Step 1: Tap the Ctrl + Alt + Delete keys to open a menu and then expand the Shutdown options which are right next to the power button.
Step 2: After that, tap and hold the Shift key and then click on Restart.
Step 3: And in the Troubleshoot menu that opens, click on the Advanced options and then go to the Startup settings.
Step 4: Click on Restart and tap F4 to select Safe Mode or tap F5 to select “Safe Mode with Networking”.
Step 5: After your PC has successfully rebooted, tap Ctrl + Shift + Esc to open the Task Manager.

Step 6: Go to the Processes tab and look for the process named “Ransomeware.exe” as well as any suspicious-looking process that could be related to this crypto-malware and then end its process.

Step 7: Exit the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 8: From the list of installed programs, look for any unknown and dubious program that could be related to the Jewsomware malware and then uninstall it.
Step 9: Close Control Panel and tap Win + E keys to open File Explorer.
Step 10: Navigate to the following locations and look for the malicious components of Jewsomware like “Ransomeware.exe” and then delete them all.
- %TEMP%
- %APPDATA%
- %Userprofile%\Robin
- %Userprofile%\Cerber
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 11: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name] this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 12: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 13: Navigate to the listed paths below and look for the registry keys and sub-keys created by Jewsomware ransomware.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\Background
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Personalization
- HKEY_CURRENT_USER\Control Panel\Desktop\ScreenSaveTimeOut
- HKEY_CURRENT_USER\Control Panel\Desktop
Step 14: Delete the registry keys and sub-keys created by Jewsomware.
Step 15: Close the Registry Editor and empty your Recycle Bin.
Try to recover your encrypted files using the Volume Shadow copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if Jewsomware ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

Once you’re done executing the steps given above, you need to continue the removal process of Jewsomware ransomware using a reliable program like [product-name]. How? Follow the advanced removal steps below.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.
- After the scan is completed click the “Fix, Clean & Optimize Now”button.