What is Wana Decryptor 2.0?
Wana Decryptor 2.0 is an alternative version of the WannaCry ransomware and a subsequent version of the Wana Decryptor ransomware. These kind of ransomware exploits the EternalBlue or the CVE-2017-0145 vulnerability. Using EternalBlue, these ransomware is able to infiltrate the computer through the backdoor and starts to encrypt files.
The Wana Decryptor made its first appearance on the 12th of May, 2017 that resulted to rampage for over 150 affected countries. It affected several big companies like the international shipping agency FedEx, the National Health Service in Britain, the Russian Interior Ministry as well as other known companies in Germany, Spain and Japan. Luckily, a“kill switch” was found by an anonymous with an alias of “MalwareTech” that have managed to terminate the ransomware for a while. However, the cyber criminals behind it have managed to patch the ranomsware’s weakness and were able to strike back again.

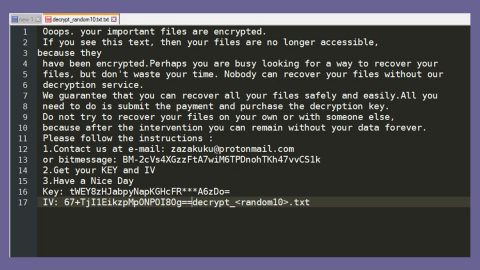
The Wana Decryptor 2.0 is disguised under Microsoft Security Center (2.0) messages. Researchers have yet to find out the encryption algorithm it uses to encrypt files. Once it infects your computer, it targets several file formats in your computer and then starts the encryption process. During that time, it appends the .wncry file extension to all the targeted files. Then it opens a window that contains the ransom note which, as you can see is quite similar to the WannaCry ransomware’s ransom note.
How is the Wana Decryptor 2.0 distributed?
According to researchers, the Wana Decryptor 2.0 is distributed through botnets. Since it uses botnets, this ransomware has a worm-like feature making it even more destructive. You should also be cautious when opening your email messages and avoid spam email. Like stated earlier, the Wana Decryptor 2.0 ransomware was able to infect big companies like FedEx, so it is possible that you’ll receive spam emails from the infected companies like this that contains the infected attachment. It uses the name of these big companies to lure you into opening the spam email and downloading the corrupted attachment. That’s why you must always take time to update your operating system as well as have a good anti malware installed on your computer like the SpyRemover Pro to prevent this kind of infection from spreading in your computer.
We’ve prepared instructions below to help you remove the pesky threat that is the Wana Decryptor 2.0. Follow them thoroughly.
Step 1: Restart your PC into Safe Mode.
Windows XP/Windows Vista/Windows 7
1. Restart your computer.
2. Press the F8 key for a couple of times to open the Boot menu.
3. Navigate to Safe Mode using arrow keys, and then press Enter.
Windows 8/Windows 8.1
1. On the Metro User Interface screen press the Power icon.
2. Tap and hold the Shift key and click on Restart.
3. Select Advanced options from the Troubleshooting menu.
4. Navigate to Startup Settings and press Restart.
5. Press the F4 key to reboot in Safe Mode.
Step 2: Open the Windows Task Manager by pressing Ctrl + Shift + Esc at the same time. Proceed to the Processes tab and look for the any suspicious processes that can be related to the Wana Decryptor 2.0 Ransomware.

Right-click on the processes, then click Open File Location and scan them using a powerful and trusted antivirus like SpyRemover Pro. After opening their folders, end their processes and delete their folders. If the virus scanner fails to detect something that you know is suspicious, don’t hesitate to delete it.
Step 3: Open Control Panel by pressing Start key + R to launch Run and type appwiz.cpl in the search box and click OK.


Locate any suspicious program and then Uninstall.
Step 4: Go to System Configuration. To open it, click the Windows button and type msconfig in the search box and hit Enter. Go to Startup and unmark items with unknown manufacturers.

Step 5: Delete everything under these directories:
-
%USERPROFILE%\Downloads
-
%USERPROFILE%\Desktop
-
%TEMP%
Step 6: Open the Registry Editor, to do so, tap Win + R and type in regedit and then press enter.
Step 7: Locate the path below and check if there is a new suspicious entry.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Step 8: If there is a new suspicious entry that can be related to the Wana Decryptor 2.0 ransomware and delete it.
Step 9: Close the Registry Editor and empty the Recycle Bin.
Step 10: Restart your PC.
Step 11: Perform a full system scan using SpyRemover Pro.
Step 12: Try to recover your encrypted files using the Windows Previous Versions feature. Take note though, this method would only work if the Wana Decryptor 2.0 hasn’t deleted the shadow volume copies of your files and if the System Restore function was enabled in your computer’s operating system.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.