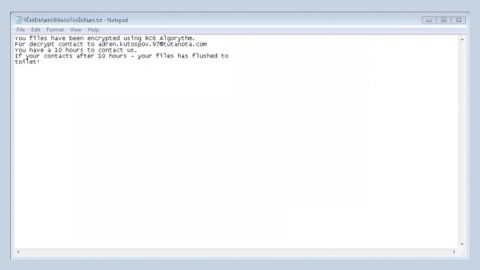
Most computer users are sure aren’t stranger to the annoyance and frustration that comes from Browser Hijacker programs such as the Congratulations Amazon User scam. This fake message is a potentially unwanted software and is widely known for its unpleasant ability to take over the user’s browsers such as Chrome, IE, Edge, Mozilla, etc. and modify them without asking for authorization from the computer’s Administrator. Commonly, the most frequently reported changes that Hijackers like Congratulations Amazon User tend to introduce to the targeted browser are the replacement of the default search engine and/or the homepage. Additionally, it is possible that new toolbars and other extensions are added to the browser and also, the pesky software might even try to trigger page redirects or generate intrusive and annoying pop-ups and ads. Usually, the only and most effective way to stop all this is to eliminate the irritating program that causes it.
Is Browser Hijacker a Virus program?
It is not new for users as well as some researchers and experts to refer this adware Congratulations Amazon User to intrusive programs as malware or viruses. But, it is considerable that Browser Hijacker aren’t exactly what you would call a “virus” unlike the other malware. You can distinguish through a few substantial differences between real software threats like Trojans, Ransomware, Spyware, etc. that can damage your PC, mess with your files or spy on you and potentially unwanted applications such as BrowsStep 1: er Hijackers. It is developed with the primary purpose of most applications that fall under the Hijacker category is the generation of money through Internet marketing/advertising, and along with that for sure, the methods they use can be quite unpleasant and in some cases might even compromise the whole security of the computer but for the most part, a typical Hijacker like Congratulations Amazon User wouldn’t really cause any actual harm to the system.
How to Remove Congratulations Amazon User Fake Message?
Step 1: Some of the steps will likely require you to exit the page. Bookmark it for later reference.
Step 2: Removing Congratulations Amazon User manually usually takes hours and may damage your system in the process. If you want a fast safe solution, we recommend SpyRemover Pro.
Press CTRL + SHIFT + ESC at the same time and go to the Processes Tab (the “Details” Tab on Win 8 and 10). Try to determine which processes are dangerous.
Right click on each of them and select Open File Location. Then scan the files with our free online virus scanner:
After you open their folder, end the processes that are infected, then delete their folders.
Note: If you are sure something is part of the infection – delete it, even if the scanner doesn’t flag it. No anti-virus program can detect all infections.
Step 3: Hold together the Start Key and R. Type appwiz.cpl –> OK.
You are now in the Control Panel. Look for suspicious entries. Uninstall it/them.
Type msconfig in the search field and hit enter. A window will pop-up:
Startup —> Uncheck entries that have “Unknown” as Manufacturer or otherwise look suspicious.
Step 4: Hold the Start Key and R – copy + paste the following and click OK:
notepad %windir%/system32/Drivers/etc/hosts
A new file will open. If you are hacked, there will be a bunch of other IPs connected to you at the bottom. Look at the image below:
If there are suspicious IPs below “Localhost” – write to us in the comments.
Open the start menu and search for Network Connections (On Windows 10 you just write it after clicking the Windows button), press enter.
- Right-click on the Network Adapter you are using —> Properties —> Internet Protocol Version 4 (ICP/IP), click Properties.
- The DNS line should be set to Obtain DNS server automatically. If it is not, set it yourself.
- Click on Advanced —> the DNS tab. Remove everything here (if there is something) —> OK.
- After you complete this step, the threat will be gone from your browsers. Finish the next step as well or it may reappear on a system reboot.
Right click on the browser’s shortcut —> Properties.
NOTE: We are showing Google Chrome, but you can do this for Firefox and IE (or Edge).

Properties —–> Shortcut. In Target, remove everything after .exe.

Step 6:
Type Regedit in the windows search field and press Enter.
nside, press CTRL and F together and type the threat’s Name. Right click and delete any entries you find with a similar name. If they don’t show up this way, go manually to these directories and delete/uninstall them:
- HKEY_CURRENT_USER—-Software—–Random Directory. It could be any one of them – ask us if you can’t discern which ones are malicious.
HKEY_CURRENT_USER—-Software—Microsoft—-Windows—CurrentVersion—Run– Random
HKEY_CURRENT_USER—-Software—Microsoft—Internet Explorer—-Main—- Random
There’s no doubt that the smartest thing you can do as a way to handle this sort of irritating, pesky and unwanted program is to simply make sure that they do not get in or installed onto your computer. Usually, this isn’t really a very complicated task where you just need to keep certain things in mind and stick to a couple of essential computer protection rules. For starters, the key aspect of maintaining a clean and secure PC is being careful with your online activities and to invest into reliable anti-malware removal tool such as SpyRemover Pro.
“use a one click solution like SpyRemover Pro”