Recently, a new bootlocker ransomware has been discovered by Malware Blocker they referred to as “RedBoot”.
What is RedBoot? And how does it function?
RedBoot is somewhat a unique kind of infection as it is contains a hybrid behavior of both a file-encrypting threat and a wiper. When executed, it encrypts files on the affected PC and replaces the MBR or Master Boot Record of the system drive and then it modifies the partition table in some kind of way. The latter is responsible how system partitions that contains files, operate. It also tends to modify hard drive partitions irrevocably. RedBoot does not provide any way to input a key to resotre the Master Boot Record and partition table, so unless the its developers has a bootable decryptor, this malware may be a wiper.
RedBoot is compiled with AutoIT executable that when executed extracts 5 other files and places them into a random folder where its launcher was executed. These 5 files are listed below.
- exe – this is a copy of the renamed file nasm.exe which is used to compile the boot.asm assembly into the MBR bin file.
- asm – this is the assembly file which is compiled into the new MBR.
- bin – after the boot.asm file is compiled by assembly.exe, boot.bin is the result.
- exe – this file is used to overwrite existing Master Boot Record with the newly compiled boot.bin file.’
- exe – this is the user mode file encrypter used to encrypt files in the computer.
- exe – this is the one responsible for terminating and preventing various programs from running in your computer such as the Task Manager and the processhacker.
After all these files are extracted, RedBoot’s main launcher will execute another command to compile the boot.asm file into the boot.bin file. After that, the launcher will get rid of the boot.asm and assembly.exe files from the computer and then use the overwrite.exe to overwrite the computer’s current Master Boot Record with the compiled boot.bin using another command. It then starts the main.exe file that scans all the directories in the computer for any files to encrypt and then it launches the protect.exe file to block any programs that can be used to analyze and stop the malware from its attack.
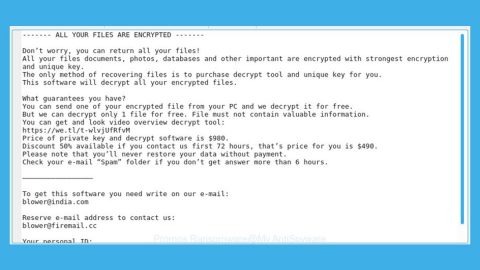
Aside from encrypting common files like images, audio, videos and so on, it also encrypts executable files, DLL files and appends the .locked extension on each file. After the encryption, the malware restarts the PC and instead of starting Windows, it displays a ransom note generated by the newly-created master boot record.
“This computer and all of it’s files have been locked! Send an email to [email protected] containing your ID key for instructions on how to unlock them. Your ID key is 79E7794CEEBBDF34EE595914D968AAAD2E355904”
The ransom note instructs its victims to send their Id to the developer at [email protected] so that they could get payment instructions. Despite this infection being new, based on preliminary analysis by security experts, it does not look promising for the victims at all since it does not only encrypt files and overwrite Master Boot Record but it also modifies the partition table without any solutions provided to restore it which means that even if you manage to restore your files, your hard drive may not be recoverable.
Eliminate RedBoot using the instructions below.
Step 1: Restart your PC to Safe Mode with Networking.

Step 2: Enable the disabled Windows features.
- Press Win + R keys to launch Run.
- Type in msc in the box and press Enter to open Group Policy.
- Under Group Policy, navigate to:
- User Configuration\Administrative Templates\System
- After that, open Prevent access to the command prompt.
- Select Disable to enable cmd
- Click the OK button
- After that, go to:
- Configuration\Administrative Templates\System
- Double click on the Prevent Access to registry editing tools.
- Choose Disabled and click OK.
- Navigate to :
- User Configuration\Administrative Templates\System>Ctrl+Alt+Del Options
- Double click on Remove Task Manager.
- And then set its value to Disabled.
Step 3: Tap Ctrl + Shift + Esc keys to open the Task Manager.
Step 4: Look for the following process by RedBoot and end all of them.
- exe
- asm
- bin
- exe
- exe
- exe

Step 5: Open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 6: Look for RedBoot or any suspicious program and then Uninstall it/them.

Step 7: Tap the Win + E keys simultaneously to open File Explorer.
Step 8: Navigate to the following locations below.
- %TEMP%
- %APPDATA%
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 9: Look for the following files and delete them.
- exe
- asm
- bin
- exe
- exe
- exe
The next step below is not recommended for you if you don’t know how to navigate the Registry Editor. Making registry changes can highly impact your computer. So it is highly advised to use PC Cleaner Pro instead to get rid of the entries that RedBoot created. So if you are not familiar with the Windows Registry skip to Step 12 onwards.

However, if you are well-versed in making registry adjustments, then you can proceed to step 10.
Step 10: Open the Registry Editor, to do so, tap Win + R and type in regedit and then press enter and then go to the following path:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Step 11: Look for suspicious registry entries created by RedBoot and delete them.
Step 12: Close the Registry Editor and empty the Recycle Bin.
Try to recover your encrypted files using their Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if RedBoot hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

To completely eliminate RedBoot and its malicious processes and files from your computer, follow the advanced guidelines below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.