What you should know about CryptoMix Ransomware?
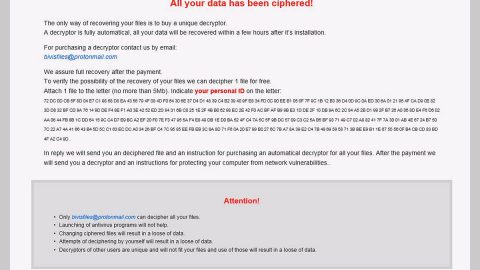
CryptoMix is another annoying file-encrypting virus discovered in spring 2016 and updated numerous times since then. Basically, this file-encrypting and ransom-demanding virus is known to appends .dg, .ck, .exte, .azer, .zayka, .noob, .cryptoshield, .mole02 and other file extensions to mark encrypted files. Once the data has been enrcypted, it drops a note – INSTRUCTION RESTORE FILES.TXT.
The updated versions of this ransomware use different ransom note names, such as _HELP_INSTRUCTION.TXT, !!!HELP_FILE!!! #, # RESTORING FILES #.HTML or # RESTORING FILES #.TXT.

Luckily, the security experts managed to break the code of a few variants and created decryption software. However, ransomware developers shortly released updated ransomware variants that cannot be decrypted through any third-party tools.
Just like earlier variants such as the CryptoMix Wallet and Azer ransomware, there recently emerged Exte ransomware virus is not decryptable yet. So it’s always better to take precautions to avoid these viruses.
This crypto-malware stealthily infiltrates one’s computers through the help of spam. Once it finds a way to enter the system, it also finds the predetermined files and encrypts them with a sophisticated RSA-2048 encryption algorithm. The malware appends originally with .email[[email protected]]id[\[[a-z0-9]{16}\]].lesli or .lesli file extension to the targeted files.
Other variants of this malware might mark encrypted files with .CRYPTOSHIELD, .code, .revenge, .scl, .rscl, .rdmk, .rmd, .wallet, .azer, .Mole02, .EXTE, .CNC, .OGONIA etc. extensions.
Upon files encryption, the ransomware displays a ransom note called INSTRUCTION RESTORE FILES.TXT where victims are asked to contact cyber criminals through the provided email address (xoomx[@]dr.com and xoomx[@]usa.com) in order to obtain the special decryption key which they usually store in some remote folder.
In order to access the decryption key, the victim has to pay a considerable certain amount of money in the form of ransom. But, you need to take care of CryptoMix removal first because it can be contagious and easily encrypt another batch of your files unknowingly. Ransomware removal tool requires an installation of the legitimate powerful malware removal program, such as SpyRemover Pro and running a full system scan with it.
This crypto-malware is similar to CryptoWall 3.0, CryptoWall 4.0 and CryptXXX viruses. However, unlike these malicious programs, CryptoMix claims that the collected profit is used for a good cause – charity.
The Cham Team ransomware developers have also been offering a “Free tech support” for those who decided to pay up the ransom. But don’t get fooled by the promises, rather, you should remember that you are dealing with real cyber criminals, so there is no need to follow their commands and support their dirty business since they won’t ever give you the decryption keys once payment has been made.
After the victim emailed the hackers, the victim is then sent a link and a password to a One Time Secret service website which they use for exchanging anonymous messages with the hackers. At first, the hackers may attempt to convince the victim to pay for the sake of a charity. Of course, we won’t find a person who is willing to pay the ransom of of a certain amount in exchange for his or her very valuable files.
Other than that, the cyber criminals may also threatening you to double the ransom if it is not paid within 24 hours. The most interesting part is that the victim can receive a discount after contacting these hackers. In any case, we do not recommend you or any victim to go that far.
What you should do id to completely get rid of CryptoMix virus as soon as you notice you cannot access your files. However, you should know that the removal of this virus will not recover your files anymore. You need to use data decryption procedure. If you are not infected so far, be sure your data is in a safe place before the ransomware hits your computer.
How to Eliminate CryptoMix Ransomware
- Tap Ctrl+Alt+Delete and choose Task Manager.
- Go to Processes tab and look for a process belonging to the threat.
- Select this malicious process and press the End Task button.
- Leave Task Manager.
- Open File Explorer (Windows Key+E).
- Find a file that might have been launched before the infection appeared, e.g. it could be in the %TEMP%, %USERPROFILE%\desktop, %USERPROFILE%\downloads, or other folders.
- Right-click the infected file and select Delete.
- Check the %APPDATA% directory for questionable executable files that could belong to the threat, e.g. AC1AFBA98D.
- Right-click the file you suspect and press Delete.
- Search for the malware’s ransom note, right-click it and select Delete.
- Navigate to the device’s Startup folders and look for suspicious files belonging to the ransomware; right-click them and press Delete.
- Leave the File Explorer.
- Empty your Recycle bin and restart the device.
How to automatically remove CryptoMix Ransomware ?
These instructions indicate how to get rid of CryptoMix Ransomware automatically. The instructions need to be applied on the infected computer.
- Turn the infected computer on. If it is turned on, restart it.
- When BIOS screen disappears after the reboot, tap F8 key repeatedly. Advanced Options menu will show up. If Windows logo appears, reboot the PC and try pressing F8 again.
- When you access Advanced Options menu, use arrow keys to navigate and choose Safe Mode with Networking. Press Enter to access the mode.

4. Wait for Windows to load Safe Mode with Networking.
5. Press and hold the Windows key and then press R key.


6. If you have pressed both keys correctly, Windows Run Box will pop up.
7. Type the following into the Open box:
explorer https://www.fixmypcfree.com/removal
Note, that there has to be a single space gap in between iexplore and http. Click OK.
8. Internet Explorer will open and a download dialog bar will appear at the bottom of your screen. Click Run to begin the installation automatically once SpyRemover Pro is downloaded.

9.Click OK if your system asks whether you want to run SpyRemover Pro software.
10. Run SpyRemover Pro and perform a full system scan.
11. Once all the malicious infections are detected, click Fix Threats. SpyRemover Pro will ask you to register the software.
12. By registering SpyRemover Pro you will also be able to protect your computer from other potential threats. Once you have registered the program, the malware will be removed. Reboot your PC to fully implement the malware removal procedure.

Basic steps of SpyRemover Pro:
Step 1. Run SpyRemover Pro installer
Click on the .exe file that just downloaded in the lower right corner of your browser window.
Step 2. Click Yes
Click Yes to accept the User Account Control settings dialog.
Step 3. Foll0w setup instructions
Follow the instructions to get SpyRemover Pro set up on your computer and you will be good to go!
“use a one click solution like SpyRemover Pro”