This past week, a ransomware attack called “NotPetya” attacked targets around the world – particularly in Ukraine and Russia. Find out everything you need to know about this dangerous new NotPetya ransomware – including how to stop it.
What is It?
NotPetya appears to be a derivative of Petya, a ransomware virus that spread last year. However, many people argue that it has more in common with the infamous WannaCry ransomware. That’s because WannaCry and NotPetya use the same Windows exploit called EternalBlue.
On June 26, the NotPetya ransomware attacked thousands of businesses in 64 countries around the world. The ransomware was first spotted in Russia and Ukraine.
How Does It Work?
The NotPetya ransomware uses the EternalBlue exploit, a vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol. This issue was patched in March 2017. However, not all systems have received the patch. The NotPetya ransomware specifically targeted unpatched systems, which included machines running Vista, 8.1, 10, Server 2008, 2012, and Server 2016.
Computers may not have received the patch for one simple reason: they need to be configured to receive patches automatically. If your PC wasn’t configured for automatic updates, then you may be vulnerable to the NotPetya problem.
That exploit, by the way, was traced back to the US National Security Agency (NSA). The hacker group “Shadow Brokers” leaked the exploit in April 2017, leading to a surge of attacks targeting the exploit.
The Attack Wasn’t Very Successful
As of June 28, the NotPetya ransomware wasn’t a very financially successful operation. A total of 29 payments, totaling $7,497, were sent to the bitcoin address associated with the attackers.
Considering NotPetya infected 300,000 computers worldwide, that’s a very low success rate.
However, the success rate of NotPetya was complicated by the fact that the email address used to verify bitcoin payments was blocked.
Don’t Send Money to the NotPetya Bitcoin Address
Ransomware attacks like to use bitcoin addresses to accept payments because they’re more anonymous than fiat currency payment methods.
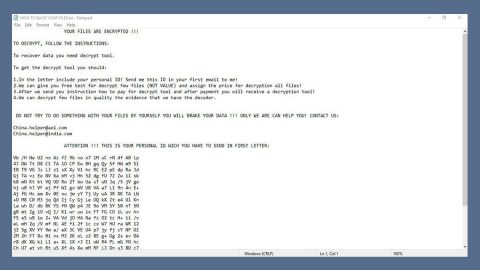
If you were infected with the NotPetya ransomware, then you may be tempted to pay the ransom and decrypt your files. However, this is a very bad idea: the email address used to verify bitcoin payments has been blocked. You can still send money to the NotPetya bitcoin address, but the attackers have no way to verify your payment – so you’re just donating money without decrypting your files. Don’t be stupid.
You Can Trick NotPetya to Not Infect your Computer
A full-scale remedy for NotPetya has not yet been identified. However, a partial solution was discovered by researcher Amit Serper. That solution only prevents NotPetya from infecting your computer if it hasn’t already done so. It won’t actually remove NotPetya from your PC or decrpy your files.
Serper’s solution is surprisingly simple: you just make a file called perfc and place it in your C:\Windows folder, then make that folder “read only”. This tricks the NotPetya malware into thinking that it’s already infected your computer.
Stay tuned for more information about a full NotPetya solution in the near future.