What is Rebus ransomware? And how does it carry out its attack?
Rebus ransomware is a new file-encrypting threat belonging to the infamous ransomware group, Scarab ransomware. It seems that developers of this ransomware group are feeling quite productive as they have released several ransomware variants as of late. According to security experts, it seems that the source code for Scarab ransomware may have been uploaded in the dark web as its variants suddenly increase in numbers in the last two months.
Rebus ransomware will initiate a series of changes in the system the moment its malicious payload is executed. These changes include creating additional malicious files to help it carry out its attack on the infected computer. It also establishes a connection to its Command and Control server and sends information about the infected computer. After these series of activities, Rebus will scan the entire drive of the system looking for files to encrypt. Just like other variants of Scarab ransomware, it mostly targets user-generated files like images, videos, documents, audio files, and many more. It uses a strong encryption algorithm in encrypting files. After the encryption, it places a text file named “REBUS RECOVERY INFORMATION.txt” to each listing folder in the system. This text file contains the ransom note that says:
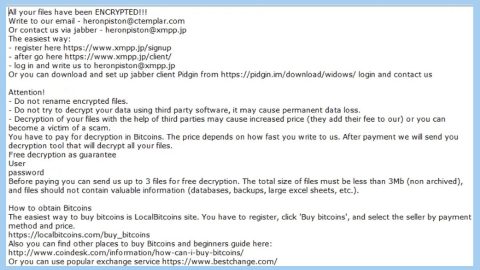
“==============================================================================”
YOUR FILES ARE ENCRYPTED!
Your personal ID
[redacted hex]
Your documents, photos, databases, save games and other important data was encrypted.
Data recovery the necessary decryption tool. To get the decryption tool, should send an email to:
[email protected] or
[email protected]
If you don’t get a reply in 24 hours use jabber:
[email protected]
The letter must include Your personal ID (see the beginning of this document).
In the proof we have decryption tool, you can send us 1 file for test decryption.
Next, you need to pay for the decryption tool.
In the response letter, You will receive the address of Bitcoin wallet which you need to perform the transfer of funds.
If you have no bitcoins
* Create Bitcoin purse: https://blockchain.info
* Buy Bitcoin in a convenient way
https://localbitcoins.com/ (Visa/MasterCard)
https://www.buybitcoinworldwide.com/ (Visa/MasterCard)
https://en.wikipedia.org/wiki/Bitcoin (the instruction for beginners)
– It doesn’t make sense to complain of us and to arrange a hysterics.
– Complaints having blocked e-mail, you deprive a possibility of the others, to decipher the computers.
Other people at whom computers are also ciphered you deprive of the ONLY hope to decipher. FOREVER.
– Just contact us, we will stipulate conditions of interpretation of files and available payment,
in a friendly situation
– When money transfer is confirmed, You will receive the decrypter file for Your computer.
Attention!
* Do not attempt to remove a program or run the anti-virus tools
* Attempts to decrypt the files will lead to loss of Your data
* Decoders other users is incompatible with Your data, as each user unique encryption key
===============================================================================”
As you can tell, Rebus ransomware uses three email addresses in communicating with its victims. However, contacting any of them is definitely not recommended as you would only end up losing money for nothing. Cyber criminals can’t be trusted so it’s best if you use other alternative ways in recovering your files rather than giving the crooks what they want.
How does Rebus ransomware proliferate?
Rebus ransomware proliferate using spam emails. Usually, ransomware developers use obfuscated files and attach them to spam emails. These obfuscated files might be ZIP files, executable files, and documents with macro scripts that are used in installing ransomware threats like Rebus. These spam emails could also contain some malicious link that redirects you to the source of ransomware infections.
Terminate Rebus ransomware from your system by following the removal guide below as well as the advanced steps that follow.
Step 1: Tap the Ctrl + Alt + Delete keys to open a menu and then expand the Shutdown options which is right next to the power button.
Step 2: After that, tap and hold the Shift key and then click on Restart.
Step 3: And in the Troubleshoot menu that opens, click on the Advanced options and then go to the Startup settings.
Step 4: Click on Restart and tap F4 to select Safe Mode or tap F5 to select Safe Mode with Networking.
Step 5: After your PC has successfully rebooted, tap Ctrl + Shift + Esc to open the Task Manager.

Step 6: Go to the Processes tab and look for any suspicious-looking processes that could be related to Rebus ransomware and then end their processes.

Step 7: Exit the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 8: Look for Rebus Ransomware and other dubious program and then uninstall them.

Step 9: Close Control Panel and tap Win + E keys to open File Explorer.
Step 10: Navigate to the following locations and look for the malicious components created by Rebus ransomware like REBUS RECOVERY INFORMATION.txt and make sure to delete them all.
- %APPDATA%
- %TEMP%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 11: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name] this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 12: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.
Step 13: Navigate to the listed paths below and look for the registry keys and sub-keys created by Rebus ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 14: Delete the registry keys and sub-keys created by Rebus ransomware.
Step 15: Close the Registry Editor and empty your Recycle Bin.
To ensure the removal of Rebus ransomware from your system including the malicious components it has created on your system, follow the advanced steps below.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.

- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.