What is PSCrypt ransomware? And how does it implement its attack?
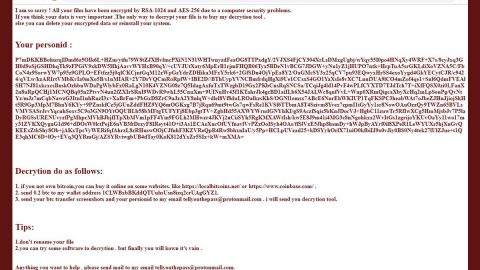
PSCrypt ransomware is a file-encrypting virus that was first discovered last year, 2017, which targeted individual users as well as organizations in Ukraine. This crypto-malware is based on the GlobeImposter ransomware. Once it is able to infect a system, a malicious file named “xls.scr” which displays a power or energy icon is dropped into the system responsible for loading PSCrypt on the infected machine. PSCrypt ransomware has the same functionalities as GlobeImposter and will exclude system folders from being encrypted. It encrypts files with specific file extensions such as .$er, .4db, .4dd, .4d, .4mp, .abs, .accdb, .accdc. And as usual, just like GlobeImposter, it uses a temporary batch file to clear the Volume Shadow Copies of the files as well as the Event Logs. One of the noticeable changes in this new variant is its ransom note called “Ваші файли тимчасово зашифрувати! Не хвилюйтесь!” – its content is quite lengthy and is as follows:
“ВАШ ЛИЧНЫЙ ИДЕНТИФИКАТОР
☠ ВАШІ ФАЙЛИ ТИМЧАСОВО НЕДОСТУПНІ.☠
ВАШІ ДАНІ БУЛИ ЗАШІВРОВАННИ!
Для відновлення даних потрібно дешифратор.
Щоб отримати дешифратор, ви повинні, оплатити послуги розшифровки:
Оплата відбувається за коштами біткойн на кошелек № 1EoWxYTt7xCskTxjm47E2XNxgkZv1anDP9
Вартість послуги складає 150$
Оплату можна провести в терміналі IBox. або виберіть один з обмінних сайтів на сторінці – https://www.bestchange.ru/privat24-uah-to-bitcoin.html (приклад обмін Приват24 на BTC) також можете скористатися послугами https://e-btc.com.ua
Додаткова інформація:
Програма можемо дешифрувати один файл як доказ того, що у неї є декодер. Для цього необхідно надіслати зашифрований файл – вагою не більше 2 mb, и ваш уникальный идентификационный код, на пошту: [email protected]
Более детальная инструкция по оплате: https://btcu.biz/main/how_to/buy
Увага!
Всі файли розшифровуються тільки після 100% оплати
Ви дійсно отримуєте дешифратор після оплати
Не намагайтеся видалити програму або запустити антивірусні інструменти це може ускладнити вам роботу
Спроби самодешіфрованія файлів приведуть до втрати ваших даних
Декодери інших користувачів не сумісні з вашими даними, оскільки унікальний ключ шифрування кожного користувача.
За запитом користувачів, надаємо контакти клієнтів, які вже користувалися послугами нашого сервісу.
ОБОВ’ЯЗКОВО ЗАПИШІТЬ РЕЗЕРВНІ КОНТАКТИ ДЛЯ ЗВ’ЯЗКУ:
[email protected] – основний
[email protected] – резервний
Додаткові контакти:
[email protected] – (якщо відповіді не прийшло після 24-х годин)
[email protected] – (якщо відповіді не прийшло після 24-х годин)
[email protected] – (якщо відповіді не прийшло після 24-х годин)
З повагою
Unlock files LLC
33530 1st Way South Ste. 102
Federal Way, WA 98003
United States”
Its English version, however, is rather short and to the point. It states:
“ALL DATA IS ENCRYPTED!
For decoding, write to the addresses:
[email protected] – Basic
[email protected] – backup
Additional Contacts:
[email protected] – (if the answer did not arrive after 24 hours)
[email protected] – (if the answer did not arrive after 24 hours)
[email protected] – (if the response did not arrive after 24 hours)”
As usual, when dealing with file-encrypting malware, paying the ransom is definitely not recommended. So the best way to deal with it is by wiping it out of your computer and use whatever backup copies you have until a free decryptor is available.
How does PSCrypt ransomware proliferate?
Just like other variants of GlobeImposter ransomware, creators of PSCrypt uses spam emails in proliferating this file-encrypting virus. More often than not, crooks tend to disguise the email as something urgent to lure users into opening them and downloading the corrupted attachment used to launch PSCrypt into the targeted system.
For the removal of PSCrypt ransomware, follow the given steps below.
Step 1: Tap Ctrl + Shift + Esc keys to launch the Task Manager.
Step 2: Go to Processes and look for the malicious process of PSCrypt ransomware then right click on it and select End Process or End Task.

Step 3: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 4: Look for dubious programs that might be related to PSCrypt ransomware and then Uninstall it/them.

Step 5: Tap Win + E to launch File Explorer.
Step 6: From there, navigate to the following directories listed below and look for the malicious components of PSCrypt ransomware like a file named “Ваші файли тимчасово зашифрувати! Не хвилюйтесь!” and an html file named “Paxynok.html” and remove them all.
- %TEMP%
- %APPDATA%
- %DESKTOP%
- %USERPROFILE%\Downloads
- C:\ProgramData\local\
Step 7: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name], this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 8: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 9: Navigate to the listed paths below and look for the registry keys and sub-keys created by PSCrypt ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 10: Delete the registry keys and sub-keys created by PSCrypt ransomware.
Step 11: Close the Registry Editor.
Step 12: Empty your Recycle Bin.
Complete the removal process of PSCrypt ransomware by using a trusted and reliable program like [product-name]. Refer to the following guidelines on how to use it.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.