What is GandCrab 5.1 ransomware? And how does it execute its attack?
GandCrab 5.1 ransomware is the latest variant of the notorious GandCrab ransomware. This new variant has been caught spreading using .JS or JavaScript files. According to security experts, the infected JS files are disguised as jpeg files that are embedded in .ZIP files attached to emails. Once this ZIP file is opened, the file named “PIC0101302924102- jpg.JS” is extracted. As a result, this .JS file will launch GandCrab 5.1 ransomware in the targeted machine using the following malicious processes:
- SHA256:dffc26736e57470e4c56e4adf3f0425080c43a136d0dd72c22075fde3efd2239
Name:TempoJB62.exe
- SHA256:be0c8cdc1937d05242c672e3e61097dd1b48466839ac0a64e883d159a8df7343
Name:2510619273.exe
One of the notable differences in this new variant is that it creates a hidden window named as “AnaLab_sucks” which contains a timer that stays for a bit. After that, it continues its attack by following the same sequence of attacks as other GandCrab variants. It starts by dropping a malicious file with the following IOCs:
Name:1.exe
Size: 361.50 Kb
MD5: E387BD817E9B7F02FA9C2511CC345F12
SHA256:39514226b71aebbe775aa14627c716973282cba201532df3f820a209d87f6df9
SHA1: 98b3ec47b64198e3604c738f8c1f4753e0afa8c7
Once this file is dropped, it will trigger a Windows component named “wmic.exe” as an administrator which allows the crypto-virus to delete the Shadow Volume Copies of the files in the infected system. It triggers the “wmic.exe” file by executing the following command in the Command Prompt as an administrator:
“C\Windows\system32\wbem\wmic.exe” shadowcopy delete”
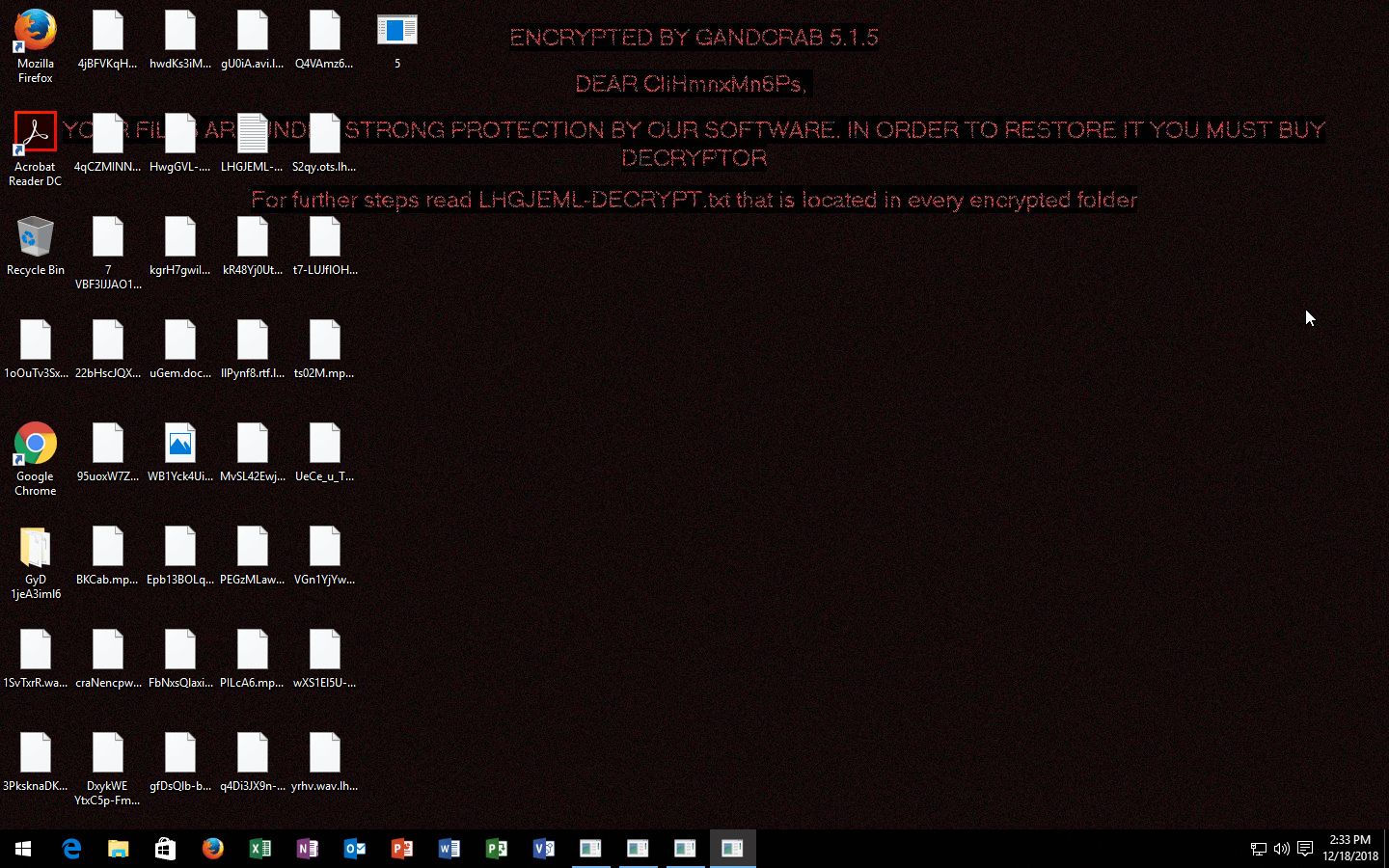
After deleting the Shadow Volume Copies of the files, it opens its ransom note named “[user’s_ID]-DECRYPT.txt” which contains the following message:
“—= GANDCRAB V5.1 =—
UNDER NO CIRCUMSTANCES DO NOT DELETE THIS FILE, UNTIL ALL YOUR DATA IS RECOVERED
FAILING TO DO SO WIL RESULT IN YOUR SYSTEM CORRUPTION, IF THERE ARE DECRYPTION ERRORS
Attention!
All your files, documents, photos, databases, and other important files are encrypted and have the extension:
The only method of recovering files is to purchase a unique private key. Only we can give you this key and only and only we can recover your files.
The server with your key is in a closed network TOR. You can get there in the following ways:
—————————————————————————————–
| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor Browser
| 2. Open Tor Browser
| 3. Open link in TOR browser http://gandcrabmfe6mnef.onion/ b6314679c4ba3647/
| 4. Follow the instructions on this page
—————————————————————————————–
On our page, you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW”
During the encryption, GandCrab 5.1 ransomware uses the Salsa20 cipher. Unlike the commonly used algorithms like RSA and AES, Salsa20 is a lot faster and can encrypt all targeted files in just a minute. Once it’s done encrypting files, it encrypts random characters to them which are the same as the victim’s user ID provided by the crypto-virus. GandCrab 5.1 ransomware skips the following Windows directories when encrypting files:
- \ProgramData\
- \Program Files\
- \Tor Browser\
- Ransomware
- \All Users\
- \Local Settings\
After the encryption, aside from displaying the ransom note given above, GandCrab 5.1 ransomware also changes the desktop wallpaper of the infected computer.
How does GandCrab 5.1 ransomware proliferate?
As pointed out earlier, GandCrab 5.1 ransomware proliferate using .JS files that are distributed via malicious spam email campaigns. According to a victim, the questionable emails contain the following content:
“From: Deanna Bennett <>
Subject: Payment Invoice #93611
Attachment: DOC402942349491-PDF.7Z
Dear Customer,
To read your document please open the attachment and reply as soon as possible.
Kind regards,
TCR Customer Support”
To successfully wipe out GandCrab 5.1 ransomware from your infected computer make sure that you follow the given removal instructions below thoroughly.
Step_1: Restart your PC and boot into Safe Mode with Command Prompt by pressing F8 a couple of times until the Advanced Options menu appears.
Step_2: Navigate to Safe Mode with Command Prompt using the arrow keys on your keyboard. After selecting Safe Mode with Command Prompt, hit Enter.
Step_3: After loading the Command Prompt type cd restore and hit Enter.
Step_4: After cd restore, type in rstrui.exe and hit Enter.
Step_5: A new window will appear, and then click Next.
Step_6: Select any of the Restore Points on the list and click Next. This will restore your computer to its previous state before being infected with the GANDCRAB V5.0 Ransomware. A dialog box will appear and then click Yes.
Step_7: After System Restore has been completed, try to enable the disabled Windows services.
- Press Win + R keys to launch Run.
- Type in gpedit.msc in the box and press Enter to open Group Policy.
- Under Group Policy, navigate to:
- User Configuration\Administrative Templates\System
- After that, open Prevent access to the command prompt.
- Select Disable to enable cmd
- Click the OK button
- After that, go to:
- Configuration\Administrative Templates\System
- Double click on the Prevent Access to registry editing tools.
- Choose Disabled and click OK.
- Navigate to :
- User Configuration\Administrative Templates\System>Ctrl+Alt+Del Options
- Double click on Remove Task Manager.
- And then set its value to Disabled.
Step_8: Open Task Manager by pressing Ctrl + Shift + Esc at the same time. Proceed to the Processes tab and look for the malicious processes of GANDCRAB V5.0 ransomware such as “wmic.exe” and “GandCrab v5.1.exe” then end them all.
Step_9: Open Control Panel by pressing Start key + R to launch Run and type appwiz.cpl in the search box and click OK to open the list of installed programs. From there, look for GandCrab 5.1 ransomware or any malicious program and then Uninstall it.
Step_10: Tap Windows + E keys to open the File Explorer then navigate to the following directories and delete the malicious files created by GandCrab 5.1 ransomware such as TempoJB62.exe, 2510619273.exe, 3449440902.exe, GandCrab v5.1.exe, putty.exe, Analysis’s Restraint, Technologyword, output.115120150.txt, 4.exe, 1.exe and [victim’s ID]-DECRYPT.txt.
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
- %TEMP%
Step_11: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech-savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use Restoro this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step_12: Tap Win + R to open Run and then type in Regedit in the field and tap enter to pull up Windows Registry.
Step_13: Navigate to the paths listed below and delete all the registry values added by GandCrab 5.1 ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\Background
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Personalization
- HKEY_CURRENT_USER\Control Panel\Desktop\ScreenSaveTimeOut
- HKEY_CURRENT_USER\Control Panel\Desktop
Step_14: Close the Registry Editor and empty your Recycle Bin.
Congratulations, you have just removed GandCrab 5.1 Ransomware in Windows 10 all by yourself. If you would like to read more helpful articles and tips about various software and hardware visit fixmypcfree.com daily.
Now that’s how you remove GandCrab 5.1 Ransomware in Windows 10 on a computer. On the other hand, if your computer is going through some system-related issues that have to get fixed, there is a one-click solution known as Restoro you could check out to resolve them.
This program is a useful tool that could repair corrupted registries and optimize your PC’s overall performance. Aside from that, it also cleans out your computer for any junk or corrupted files that help you eliminate any unwanted files from your system. This is basically a solution that’s within your grasp with just a click. It’s easy to use as it is user-friendly. For a complete set of instructions in downloading and using it, refer to the steps below
Perform a full system scan using Restoro. To do so, follow the instructions below.