What is Unikey ransomware? And how does it work?
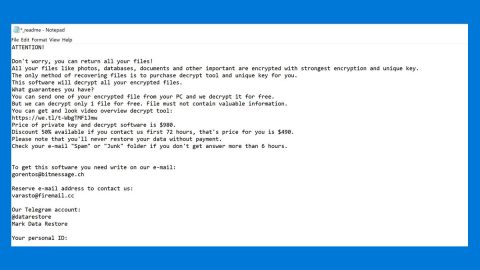
Unikey ransomware is a new file-encrypting threat and is one among the ransom ware spawned by the Hidden Tear open source platform. Unlike the other variants of the Hidden Tear platform, Unikey includes several changes to the way it works that makes it a sophisticated variant. This virus encrypts files using the AES 256 cryptographic algorithm and appends the .locked file extension on the targeted files. After the encryption process, it creates its ransom note on a text file named READ_IT.txt which contains the following message:
“Files has been encrypted with hidden tear
Send me some bitcoins or kebab
And I also hate night clubs, desserts, being drunk”
Based on its ransom note you can’t probably tell that if the crooks behind Unikey is either trying to scare you or trying to make you laugh. Clearly, its ransom note might be some sort of a joke and gives you an idea that this ransomware is developed by some inexperienced programmer. Nevertheless, despite having a joke of a ransom note, you still shouldn’t belittle this ransomware for it still can do damage to your files and it is still considered as a dangerous infection. What makes it dangerous is not only its ability to encrypt your files but also its ability to delete the shadow volume copies of your files. Meaning to say, decrypting your files using the Windows Previous Versions feature won’t work this time so you may have to look for a decryption tool. That’s why it is important to take preventive measures to make sure that your data is protected against the likes of Unikey ransomware. To do so, you should create backup copies of your important files and store them on a different location. That way you won’t have to worry how to recover your files.
How is Unikey ransomware distributed?
A Spam email with infected attachments is how Unikey ransomware spread their malicious file. The spam emails are often disguised as if it came from a well-known person or company to lure you into opening the email and download the infected attachment. These attachments are often corrupted Microsoft document files (.docx) which contains a corrupted script or macro that is used to carry out the attack and to connect to a remote server.
To avoid these kinds of infiltration, it is important that you keep your system updated since most of these attacks prey on a weak system. However, you should avoid installing these system updates from shady sites. For instance, you are redirected to a website that suggests you to install a software update. If that happens close the tab or the browser immediately. To get rid of those redirects, use a trusted antivirus program like SpyRemover Pro that automatically blocks the shady site before it opens.
Terminate Unikey ransomware using the complete set of instructions below in order to continue using your computer safely. Keep in mind that ransomware often spreads in a bundle with other types of malicious infection.
Step 1: Open Windows Task Manager by pressing Ctrl + Shift + Esc at the same time.

Step 2: Go to the Processes tab and look for any suspicious processes and then kill them.

Step 3: Open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 4: Look for Unikey Ransomware or any suspicious program and then Uninstall.

Step 5: Hold down Windows + E keys simultaneously to open File Explorer.
Step 6: Go to the directories listed below and delete everything in it. Or other directories you might have saved the file related to Unikey Ransomware.
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
- %TEMP%
Step 7: Look for READ_IT.txt and other malicious file that might be related to Unikey ransomware.
Step 8: Right-click on it and click Delete.
Step 9: Empty the Recycle Bin.
Follow the continued advanced steps below to ensure the removal of the Unikey Ransomware:
Perform a full system scan using SpyRemover Pro.
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit ENTER
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
8. A dialog box will be displayed by Internet Explorer. Click Run to begin downloading SpyRemover Pro. Installation will start automatically once download is done.

- Click OK to launch SpyRemover Pro.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register SpyRemover Pro to protect your computer from future threats.