What is Sigma ransomware? And how does it carry out its attack?
Sigma ransomware a new version of a crypto-malware that was first spotted last year. Apparently, its developers decided to update this ransomware as it was caught spreading in a new malicious spam email campaign pretending to be from Craigslist. These emails pretend to be responses to a short term job posting on Craigslist called “Gigs”. This kind of technique is not so different from the previous malicious spam email campaign used by Sigma ransomware before. This time around, Sigma ransomware attaches password protected Word or RTF documents in the email that’s supposed to contain the information regarding the respondent. Once a user opens the attachment and key in the password to the document, a screen will be displayed that asks the user to enable the content in the document. And when the user clicks on the enable content button, the embedded VBA script will be executed which will download and install Sigma ransomware into the targeted computer – during this process, the malware downloads a password protected RAR file and extract it into the %Temp% folder and then launch the extracted executable file named svchost.exe. This malicious executable file is the executable file for Sigma ransomware that will start to execute its attack.
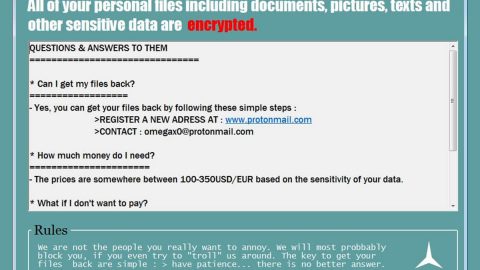
During the infiltration of Sigma ransomware, it will start to search for certain files in the affected computer. It may target popular file types that are mostly user-generated like images, videos, audio, documents, etc. Unlike its previous version, this Sigma ransomware does not append new extension to the affected files but will include a file marker instead as well as an encrypted key at the bottom of each encrypted file. while it encrypt files, it also creates ransom notes named as “ReadMe.txt” and place them in each folder where there’s an encrypted file. The ransom note contains detailed information on how to connect to the TOR payment site of the ransomware that states the following message:
“What has happened to my files ? Why i am seeing this ?
All of your files have been encrypted with RSA 2048 Encryption. Which means, you wont be able to open them or view them properly. It does NOT mean they are damaged.
Solution
Well its quite simple only we can decrypt your files because we hold your RSA 2048 private key. So you need to buy the special decryption software and your RSA private key from us if you ever want your files back. Once payment is made, you will be given a decrypter along with your private key , once you run that , All of your files will be unlocked and back to normal.
So there are 2 ways to do this either you wait for a miracle and get your price doubled or follow instructions below carefully and get back your all important files.
Payment procedure
First try to open decrypter page in normal browser
http://yowl2ugopitfzzwb.onion.link
Wait a few seconds, and site will open then enter your GUID mentioned below and process.
660F187B8C71F670E76F70C7EDAFE4E7
If you failed to open links in normal browsers
Download a special browser called “TOR browser” and then open the given below link. Steps for the same are –
- Go to https://www.torproject.org/download/download-easy.html.en to download the “TOR Browser”. 2. Click the purple button which says “Download TOR Browser” 3. Run the downloaded file, and install it. 4. Once installation is completed, run the TOR browser by clicking the icon on Desktop. 5. Now click “Connect button”, wait a few seconds, and the TOR browser will open. 6. Copy and paste the below link in the address bar of the TOR browser.
http://yowl2ugopitfzzwb.onion/
Now HIT “Enter”
- Wait a few seconds, and site will open then enter your GUID mentioned below and process.
660F187B8C71F670E76F70C7EDAFE4E7
If you have problems during installation or use of Tor Browser, please, visit Youtube and search for “Install Tor Browser Windows” and you will find a lot of videos.”
At the time of writing, there is still no way to decrypt the files affected by Sigma ransomware but that doesn’t mean that you should resort to paying the ransom.
How does Sigma ransomware proliferate?
Like pointed out, Sigma ransomware proliferates through malspam campaign that pretends to be a response from Craigslist regarding a short term job postings called Gigs.
Refer to the following instructions to terminate Sigma ransomware from your system.
Step 1: Launch the Task Manager by simply tapping Ctrl + Shift + Esc keys on your keyboard.
Step 2: Under the Task Manager, go to the Processes tab and look for a malicious process called svchost.exe which takes up most of your CPU’s resources and then end its process.

Step 3: After that, close the Task Manager.
Step 4: Tap Win + R, type in appwiz.cpl and click OK or tap Enter to open Control Panel’s list of installed programs.
Step 5: Under the list of installed programs, look for Sigma ransomware or anything similar and then uninstall it.

Step 6: Next, close Control Panel and tap Win + E keys to launch File Explorer.
Step 7: Navigate to the following locations below and look for Sigma ransomware’s malicious components such as svchost.exe and ReadMe.txt and other suspicious files contained in the following directories then delete all of them.
- %TEMP%
- %WINDIR%\System32\Tasks
- %APPDATA%\Microsoft\Windows\Templates\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
- %UserProfile%\AppData\Roaming\Microsoft\
- %UserProfile%\AppData\Roaming\tor\
Step 8: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 9: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 10: Navigate to the following path:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\chrome Rundll32.exe SHELL32.DLL,ShellExec_RunDLL %UserProfile%\AppData\Roaming\Microsoft\660F187B8C71F670E76F70C7EDAFE4E7\taskwgr.exe -p252589
Step 11: Delete the registry keys and sub-keys created by Sigma ransomware.
Step 12: Close the Registry Editor and empty the Recycle Bin.
It is important to make sure that nothing is left behind and that Sigma ransomware is completely wiped out from your system. To do that, use the following antivirus program.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.