What is Revolution ransomware? And how does it execute its attack?
Revolution ransomware is a new crypto-malware that encrypts files leaving them inaccessible to users. In order to recover them, users must pay the demanded ransom. It enters the computer system using an email attachment. Once the attachment is opened, the ransomware immediately connects to its Command and Control server to download Revolution ransomware and install it on the compromised computer.
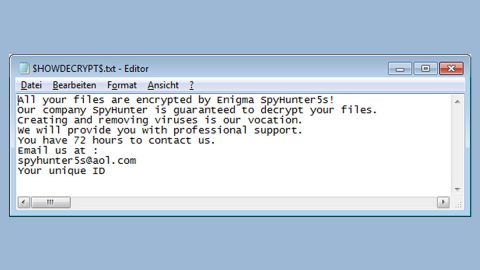
After its successful infiltration, Revolution ransomware scans the entire directories in the computer looking for files to encrypt. During the encryption, it appends the .REVOLUTION extension on all the affected files. The ransomware claims to be using the RSA 1024 encryption algorithm in encrypting files. After the encryption, it drops the InfoFiles.txt on the desktop which contains its ransom note:
“All your important files were encrypted on this PC.
All files with .revolution extension are encrypted.
Encryption was produced using unique private key RSA-1024 generated for this computer.
To decrypt your files, you need to obtain private key + decrypt software.
The single copy of the private key, with will allow you to decrypt the files, is locate on a secret server on the internet.
To retrieve the private key, you need to contact us by email [email protected] send us an email your InfoFiles.txt file and wait for further instructions.
For you to be sure, that we can decrypt your files – you can send us a 1-2 not very big encrypted files and we will send you back it in a decrypted form free.
To send files you can use xxxx://dropmefiles.com/
Do not waste your time! After 72 hours the main server will double your price!
Your personal id:
wQWg6WdxLZ8nJhND9yOFgrvc2X5mdzak21V2gm
E-mail address to contact us:
[email protected]
Reserve email address to contact us:
getyourfilles[at]india.com”
How does Revolution ransomware disseminate its infected file?
Revolution ransomware disseminates its malicious file using spam emails. These kinds of emails are mostly disguised as something important. Perpetrators often put a catchy subject telling users that it is an urgent matter and that the attachment must be downloaded. Revolution ransomware either uses a ZIP file or a document file as its attachment which is used to launch its attack on the victim’s computer. To ward off these kinds of attacks it is advisable to always keep both your antivirus program and your operating system up-to-date.
To terminate Revolution ransomware, follow the given instructions below carefully.
Step 1: Tap Ctrl + Shift + Esc to open the Task Manger.

Step 2: Once you’ve opened the Task Manager, go to the Processes tab and look for Revolution ransomware’s process and end it.
Step 3: Open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 4: Look for Revolution ransomware or any suspicious program and then Uninstall it/them.

Step 5: Tap Win + E keys to launch File Explorer.
Step 6: Navigate to the following locations below and look for Revolution ransomware’s malicious components such as InfoFiles.txt and other suspicious files and then delete all of them.
- %TEMP%
- %APPDATA%
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 7: Close the File Explorer. Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 8: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 9: Navigate to the following path:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Step 10: Delete the registry keys and sub-keys created by Revolution ransomware.
Step 11: Close the Registry Editor and empty your Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if Revolution ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

To make sure that nothing is left behind and that the Revolution is completely removed, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.