Aleta ransomware is another pesky malware infection that encrypts important files and extort ransom payment from the victims. All the corrupted files are renamed and appended with a malicious extension .[email address].aleta. Presently, Aleta ransomware is associated with [email protected] and [email protected] email addresses and a ransom note file called !#_READ_ME_#!.inf. By simply removing the threat from the infected computer, victims will basically prevent additional data and system damage.
How Does Aleta Ransomware Virus Infiltrate the System?
The main Aleta Ransomware Virus infection method is basically through exploiting the RDP protocol and services, which are used to remote control devices in internal networks and all over across the Internet.
It is reported that the Aleta has hit mostly home-owned NAS devices, because they are used to store personal files and documents. Technically, it is suspected that the attacks were simply made in an automated way by using stored software exploits.
It is also distributed through email spam messages that utilize social engineering tricks. Those behind the virus aims to confuse the targets into infecting themselves with a malware. This is done by acting as rogue website or program resembling a famous company. Aleta Ransomware is either directly attached or linked or bundled somewhere in the body contents.
The ransomware can also be injected in a payload that infects the victim’s computer upon user interaction. Usually, they come in the form of documents or software installers. When office documents such as spreadsheets, rich text documents, databases and etc. are the ones concerned the infection is done through launching the built-in macros.
There are dangerous web scripts such as redirects, ad networks and code inserted by browser hijackers that can also lead to an active Aleta virus infection with or without you even knowing.
How does the Aleta Ransomware works?
Malware rexperts identified a new BTCWare strain of virus called Aleta Ransomware that basically encrypts sensitive user data and then extorts ransom from the victims.
This new BTCWare update primarily alters some of the initial settings that are used by the engine.
Basically, it uses a new extension and a hacker-designated support email as well, while at the meantime follows the same infection routine. Once infected, the Aleta рansomware virus then automatically starts to process system and user files depending on a built-in list of popular file type extensions. Most likely, the hackers tend to endanger the most popular data like the music, videos, photos, documents, databases, backups and etc.
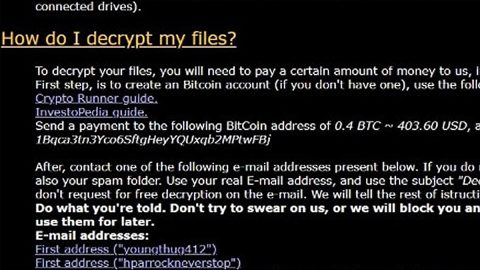
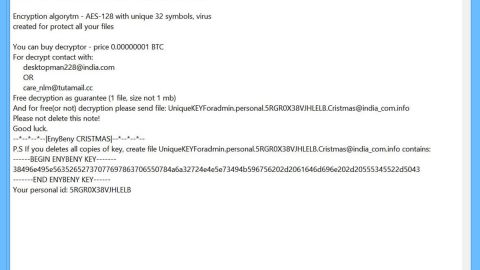
When this process is complete a ransomware note is crafted in a “!#_READ_ME_#!.inf” file that reads the following message:
[WHAT HAPPENED] Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: [email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE] Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 1Mb [HOW TO OBTAIN BITCOINS] The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller
by payment method and price
https://localbitcoins.com/buy_bitcoins [ATTENTION] Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 36 hours – your key has been deleted and you cant decrypt your filesYour ID:
bv/T6B2JQtWhZfgoT517sxu76dUOzjz7pw7slt3SWh9r8P1/FiHb1ONR7vhJ7mzWAr7GkijLUoFJkliCBLrT7605y6S2nSiQtz3Yz2J5NlOTZJBbI2drLUltZAMO+0LHOHHSfofVZK/NMBo0mkceyili2Yo/SJ4TrTtUlBE3hYE=
The Aleta virus mainly renames victim files using the file extension pattern: .[email address].aleta. A particular example used by the ransomware is .[[email protected]].aleta and it is made up of two components – The [email protected] hacker-supplied contact address and the .aleta extension. The email address is mainly hosted on QQ which is a popular service used in China. So, the .aleta extension is the final addition to the files.
Some of the reports say that the Aleta virus does not just encrypt files and merely renames them. However, it is also possible that the hackers have created several different versions.
Additionally, the Aeta ransomware is basically developed to drop an image file and modify values in Windows registry to set it as a desktop wallpaper. It depicts the following message:
ALETA RANSOMWARE
Your important files produced on this computer have been encrypted!
The only way to decrypt your files is to receive the private-key and decryption program.
To receive the private-key and decryption program write us to the e-mail: [email protected] and attach your ID
You can find it in READ_ME file
ATTENTION!
If you not write on e-mail in 36 hours your key has been deleted and you cant decrypt your files
The victims can effectively remove the threat through using a quality anti-malware solution if not removing it manually. The affected data can then be recovered using a professional-grade solution as well.
How to manually remove Aleta Ransomware?
- Press Ctrl+Shift+Esc and click Processes.
- Check the list of processes and kill those you find suspicious.
- Press Win+R and type regedit.exe in the command line.
- Click OK or press Enter.
- Locate the Value Wallpaper in HKCU\Control Panel\Desktop, double-click it, and clear the Value data field.
- Click OK.
- Open HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aleta and remove this registry key.
- Close Registry Editor and open Explorer (tap Win+E).
- Delete !#_READ_ME_#!.inf from the following directories:
- %ALLUSERSPROFILE%\Start Menu
- %APPDATA%\Microsoft\Windows\Start Menu
- %USERPROFILE%\Microsoft\Windows\Start Menu
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu
- Delete all suspicious files from %USERPROFILE%\Desktop, %USERPROFILE%\Downloads, and %TEMP% directories.
- Empty the Trash bin.
Hot to automatically remove Aleta ransomware?
These instructions indicate how to get rid of Aleta Ransomware automatically. The instructions need to be applied on the infected computer.
- Turn the infected computer on. If it is turned on, restart it.
- When BIOS screen disappears after the reboot, tap F8 key repeatedly. Advanced Options menu will show up. If Windows logo appears, reboot the PC and try pressing F8 again.
- When you access Advanced Options menu, use arrow keys to navigate and choose Safe Mode with Networking. Press Enter to access the mode.

4. Wait for Windows to load Safe Mode with Networking.
5. Press and hold the Windows key and then press R key.


6. If you have pressed both keys correctly, Windows Run Box will pop up.
7. Type the following into the Open box:
explorer https://www.fixmypcfree.com/removal
- Note, that there has to be a single space gap in between iexplore and http. Click OK.
8. Internet Explorer will open and a download dialog bar will appear at the bottom of your screen. Click Run to begin the installation automatically once SpyRemover Pro is downloaded.

9. Click OK if your system asks whether you want to run SpyRemover Pro software.
10. Run SpyRemover Pro and perform a full system scan.
11. Once all the malicious infections are detected, click Fix Threats. SpyRemover Pro will ask you to register the software.
12. By registering SpyRemover Pro you will also be able to protect your computer from other potential threats. Once you have registered the program, the malware will be removed. Reboot your PC to fully implement the malware removal procedure.