What is ABC ransomware? And how does it execute its attack?
ABC ransomware is a recently-discovered crypto-malware that stealthily infiltrates computer systems. Since this ransomware’s activity is low, security experts are still puzzled and trying to figure out what ransomware group ABC ransomware belongs to but if you observe its appended file extension, it might actually refer to the Globe Imposter virus – developers of this malware keeps on bothering the virtual community by creating new versions of crypto-malware every now and then. On the other hand, there is also a possibility that ABC ransomware is related to ABCLocker which emerged in summer this year and it seems to be an independent crypto-malware.
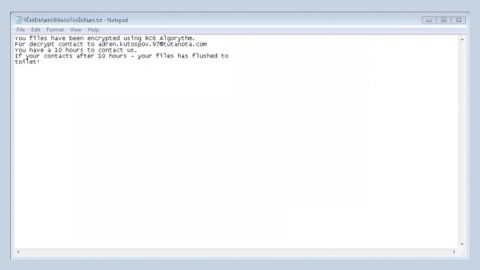
Just like other ransomware infections, ABC ransomware functions as a file-encrypting threat that makes use of both RSA and AES ciphers to encrypt its targeted files. During its invasion, it looks for the following file formats on the entire computer drive:
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpeg; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc;
As you can see, this ransomware is quite threatening as it targets various file formats. During the encryption, it applies the RSA and AES encryption algorithm to leave files unreadable and then append random 8 characters to every affected file. It leaves a text file named READ_IT.html on every folder where there is an encrypted file. It contains the ransom message that reads as follows:
“All your files have been encrypted!
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Decryption as guarantee
Your documents, photos, databases and other important files have been encrypted cryptographically strong, without the original key recovery is impossible! To decrypt your files you need to buy the special software – “DECRYPTER” Using another tools could corrupt your files, in case of using third party software we dont give guarantees that full recovery is possible so use it on your own risk. If you want to restore files, go to on our site: 1) Download TOR-Browser (hxxps://www.torproject.org/download/download) 2) Run it 3) Go to hxxp://cr7icbfqm64hixta.onion
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Wait from us for reply to your mail within 48 hours.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Your personal ID: -“
How is ABC ransomware disseminated?
Since the activity of this ransomware is still low, it’s still hard to tell how it is disseminated exactly. However, it might be spreading in spam emails as an infected attachment like a macro-enabled document or a malicious executable file. That’s why you have to be careful in opening any kind of emails especially if you don’t know the sender or if the sender is representing a well-known group or company. It is also important that you keep both your antivirus program and system updated always so that you can prevent the infiltration of ransomware infections.
Obliterate ABC ransomware using the complete set of instructions below in order to continue using your computer safely. Keep in mind that these kinds of infections often spread in a bundle with other types of malicious infection.
Step 1: Open Windows Task Manager by pressing Ctrl + Shift + Esc at the same time.

Step 2: Go to the Processes tab and look for any suspicious processes and then kill them.

Step 3: Open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 4: Look for ABC Ransomware or any suspicious program and then Uninstall them.

Step 5: Hold down Windows + E keys simultaneously to open File Explorer.
Step 6: Go to the directories listed below and look for the ransom note named READ_IT.html as well as other malicious files created by ABC ransomware and remove them.
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
- %TEMP%
Step 7: Close the File Explorer.
Step 8: Empty the Recycle Bin.
Try to recover your encrypted files using their Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if the crypto-malware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

To make sure that nothing is left behind and that the ABC ransomware is completely removed, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOSscreen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Optionuse the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Boxwill show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.