What is ACCDFISA v2.0 ransomware? And how does it execute its attack?
ACCDFISA v2.0 ransomware is a new file-encrypting Trojan that originates from the ACCDFISA ransomware family. The first version of the ACCDFISA ransomware was first released way back in 2016. And apparently its developers decided to strike again with version number 2 this year. The ransomware still uses the same tactic which involves using brute-force Remote Desktop Protocol ports to break into the system.
As of October 2017, IT experts have detected a hike in ACCDFISA v2.0 ransomware’s activity again after its first attack on 2016. This ransomware is also known as “Anti-Child Porn Spam Protection” (ACCDFISA) which operates differently compared to other ransomware threats as it does not employ a specific cipher to encrypt files. What it does is it compresses the targeted files into .RAR files and locks them with a password. It targets files with the following file extensions:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
Each of the affected files are transformed into an executable file (.exe) which still bears their original file names but this time with the IR number as well as the perpetrator’s email address. The latest ACCDFISA v2.0 uses the following email addresses:
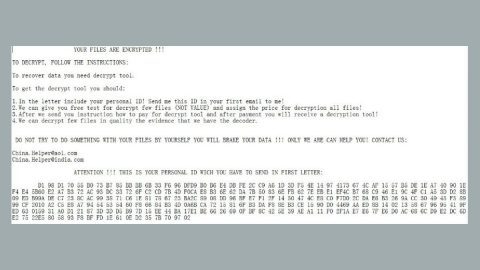
Before it starts the encryption, there are other tasks this ransomware executes – the first one is that it is downloaded as .RAR or .ZIP folder which contains a specific script that executes ACCDFISA v2.0 ransomware. It also extracts its malicious components into C:\Windows\System32 folder in 64-bit systems or into C:\Windows\SysWOW64 in 32-bit systems. This ransomware also modifies the Registry files and creates its own registry keys and sub-keys. In addition, ACCDFISA v2.0 ransomware also functions as a screen-locker as it locks the screen right after it finishes the encryption process and opens a program window that contains the following message:
“Warning! Access to your computer is limited and all your important files has been decrypted with AES-256-KEY.
A mailing (spam) was detected on your computer that was sending a very dangerous polymorphic virus, which contradicts the law and harms other network users. Your computer has been also infected by this very dangerous polymorphic virus, which modifies itself every 24 hours and in this case virus detection by antiviruses is very difficult.
You need to buy and send an sms with MoneyPak or Paysafecard or Ukash code ($300 or 300 euros) and your Reference Number to our special service phone number or email.
After that, our experts within 1-3 hours will perform an audit to clean up your computer from this very dangerous polymorphic and send you sms on the cell phone or email (from which you sent the code and reference number) password (which unlocks your computer and decrypts your files) and this must be entered below.”
Worry not, as this ransom note is full of lies. You can still recover your files using other alternative methods which will be discussed later on.
How does ACCDFISA v2.0 ransomware target a computer?
As pointed out earlier, ACCDFISA v2.0 ransomware uses brute-force Remote Desktop Protocol ports in targeting computers so it would be best if you always keep your antivirus and anti malware programs as well as your system up-to-date to keep your computer safe from these kinds of attacks.
For ACCDFISA v2.0 ransomware elimination, follow the removal guide below.
Step 1: Tap Ctrl + Alt + End keys at the same time. This command launches the task menu on the remote server instead of your local PC.
Step 2: Click on the “Change a Password” menu to change your password.
Step 3: After changing your computer’s password, log into your computer and tap Ctrl + Shift + Esc keys to launch the Task Manager.
Step 4: Go to Processes and look for ACCDFISA v2.0 ransomware’s malicious process, right click on it and select End Process or End Task.

Step 4: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 5: Look for dubious programs that might by related to ACCDFISA v2.0 ransomware and then Uninstall it/them.

Step 6: Tap Win + E to launch File Explorer.
Step 7: After opening File Explorer, navigate to the following locations below and look for ACCDFISA v2.0 ransomware’s malicious components.
- C:\ProgramData\local\svchost.exe
- C:\ProgramData\local\undxkpwvlk.dll
- C:\ProgramData\local\vpkswnhisp.dll
- C:\Decrypt\Decrypt.exe (decryption tool)
Step 8: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 9: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 10: Navigate to the listed paths below and look for the registry keys and sub-keys created by ACCDFISA v2.0 ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 11: Delete the registry keys and sub-keys created by ACCDFISA v2.0 ransomware.
Step 12: Close the Registry Editor.
Step 13: Empty your Recycle Bin.
Try to recover your encrypted files using their Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if ACCDFISA v2.0 hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

In addition, you could also go to this link Karwos[.]net/accdfisa20/ for a free decryption tool.
To make sure that ACCDFISA v2.0 is completely removed and that nothing is left behind, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOSscreen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Optionuse the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Boxwill show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.