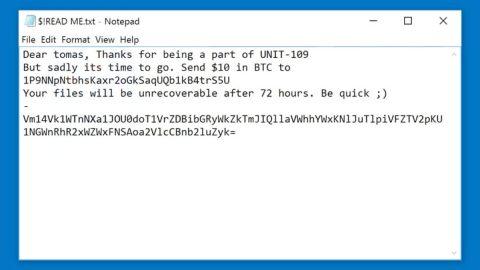
One of the best parts about phishing scams is that they’re easy to stop. You’ll see a story on the internet about how some “Nigerian prince” swindled some idiot in a developed country out of thousands of dollar.
You laugh and think, “Haha! There’s no way I’m dumb enough to fall for a phishing attack like that. How are people so dumb and I am so smart?”
Well, I’ve got some bad news for you, buddy: a new phishing attack is making the rounds on the internet, and it’s making a lot of so-called PC security experts feel dumber than ever before.
That scam has already tricked a number of major Wall Street businesses and it could probably trick you too. Here’s how the scam works:
1) You receive an email from the address of someone you know
2) The email mentions mergers or acquisitions that are already in progress, like things your business could currently be working on.
3) To make the email look extra legitimate, it will bcc other recipients.
4) The emails appear to be written by native English speakers and don’t feature the usual broken English that makes fraudulent emails obvious.
5) The emails contain Microsoft Office documents that you’ve already exchanged in an earlier email or email thread. However, these Microsoft Office documents have been edited to contain a “hidden malicious macro.” In other cases, the emails contain a simple link.
This hidden malicious macro has one goal: steal your Outlook password. Once the attackers have that information, they have full access to your email account.

Made by “Extremely Tech Savvy” Individuals
We typically associate phishing attacks with poor English skills and suspicious-looking emails.
This phishing scam has neither of those things. Instead, it uses conversational English and goes to great lengths to not appear malicious.
It also uses lingo and jargon common among those who work in financial industries – which suggests that someone has an intimate knowledge of the field and its possible weaknesses.
Ultimately, all of these things have combined to create an attack that is hard for even tech professionals to detect.
The Secret FIN4 Group “Spearphishes” for Specially Targeted Individuals
Apparently, all of these attacks have been led by a group known as FIN4. These members have been working since 2013 and have managed to remain under the radar.
In FireEye’s report on the FIN4 attacks, they claim that FIN4 uses “spearphishing” tactics. Instead of sending mass emails to a large group of people, FIN4 specially targets individuals.

Ultimately, the scam is currently estimated to have penetrated the email addresses of more than 100 companies.
Affected individuals include “C” level executives, legal counsel, scientists, and advisors for over 100 companies.
That’s bad news because the affected email addresses could contain sensitive information about mergers, acquisitions, and business financials. You know – information that certain groups of people would pay a lot of money for.

Think you can spot the scam? Read this email
If you’ve read up to this point, then you’re probably still thinking, “Haha, I’m not dumb enough to fall for this scam!”
If you still feel that way, read this email:

Honestly, that would fool me. It’s the little details that make a big difference. Things like “It is the second one in the thread.” Furthermore, there’s no attached document, no link to download a .rar file. It’s just a link to a “forum thread.”
Once you’ve clicked on that link, your computer is infected and you’re in big trouble.
Since this is a spearphishing attack, your computer will probably not be targeted by this scam unless you work on Wall Street or for some other major financial center. Still, you should stay aware of the issue, educate yourself on anti-phishing techniques, and install a good antimalware software along with PC Cleaner Pro just to make sure.