What is Rapid ransomware? And how does it execute its attack?
Rapid ransomware is an encryption Trojan first discovered on the second day of January this year. This ransomware is kind of different from a typical ransomware infection as it still remains active on the system and still continues to infect many users. Even after it encrypts the targeted files in a system, it still stays active and encrypts new files in the system – though this is not really an unusual behavior for ransomware, it is the kind of behavior that not many ransomware threats possess.
Despite being active for a long time now, it still remains a mystery how this ransomware is being distributed. But based on the reports, it has been infecting numerous users and there have been over 300 submissions of its attacks – this number is not even accurate as it might have infected more users.
The minute it enters a system, it will eliminate all the shadow volume copies in Windows, terminate database processes as well as disable automatic repair. The processes that it terminates are sql.exe, sqlite.exe and oracle.com while it also executes the following commands:
- exe Delete Shadow /All /Quiet
- exe /C bcdedit /set {default} recoveryenabled No
- exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
After it executes terminate system processes and execute commands, it will scan the computer for files to encrypt, which according to researchers, are files with the following extensions:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
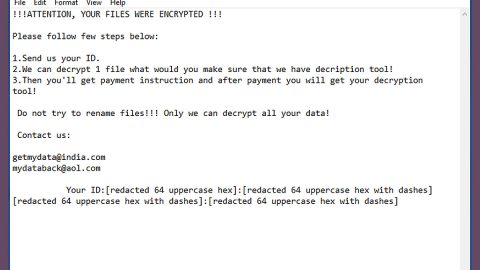
It encrypts the targeted files using the AES cryptography and appends the .rapid extension on the affected files. It then creates a ransom note in a file called How Recovery Files.txt which is placed on various folders. This text file contains a message that reads:
“Hello!
All your files have been encrypted by us
If you want to restore files write on e-mail – [email protected]”
In addition, Rapid ransomware also creates autoruns that launches the ransomware on startup and displays the ransom note. Victims are asked to contact the given email address in the ransom note to receive payment instructions. If you are one of the unfortunate ones who got infected with this ransomware, paying the ransom is not recommended; cybercrooks can’t be trusted ever. Even though Rapid ransomware can’t be decrypted for free this time, that still shouldn’t be a reason for you to go ahead and reach out to the attackers. For the meantime, use whatever backup copy you have of your affected files and wait until a free decryptor is up for grabs.
How does Rapid ransomware spread online?
Like pointed out, it isn’t clear yet how Rapid ransomware spreads. Nevertheless, you should keep an eye for any suspicious-looking spam emails as this is one of the most common distribution methods for ransomware threats. Spam emails sent out by crooks often contain malicious attachments or links used to download the ransomware infection into the system.
Wipeout Rapid ransomware from your system by following the removal guide below as well as the advanced steps that follow.
Step 1: Tap the Ctrl + Alt + Delete keys to open a menu and then expand the Shutdown options which is right next to the power button.
Step 2: After that, tap and hold the Shift key and then click on Restart.
Step 3: And in the Troubleshoot menu that opens, click on the Advanced options and then go to the Startup settings.
Step 4: Click on Restart and tap F4 to select Safe Mode or tap F5 to select Safe Mode with Networking.
Step 5: After your PC has successfully rebooted, tap Ctrl + Shift + Esc to open the Task Manager.

Step 6: Go to the Processes tab and look for rapid.exe or info.exe and then end its process.

Step 7: Exit the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 8: Look Rapid Ransomware and then uninstall it.

Step 9: Close Control Panel and tap Win + E keys to open File Explorer.
Step 10: Navigate to the following locations and look for the malicious components created by Rapid ransomware such as info.exe, How Recovery Files.txt and recovery.txt and make sure to delete them all.
- %APPDATA%
- %TEMP%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 11: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 12: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 13: Navigate to the listed paths below and look for the registry keys and sub-keys created by Rapid ransomware.
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Encrypter”=”%AppData%\info.exe”
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “userinfo”=”%AppData%\recovery.txt”
Step 14: Delete the registry keys and sub-keys created by Rapid ransomware such as info.exe and recovery.txt.
Step 15: Close the Registry Editor and empty your Recycle Bin.
To make sure that Rapid ransomware is completely removed and that nothing is left behind, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the Safe Mode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. The installation will start automatically once a download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.